SAP Security Patch Day June 2021: Multiple Memory Corruption Vulnerabilities Can Lead to System Crashes

Highlights of June SAP Security Notes analysis include:
- June Summary—20 new and updated SAP security patches released, including two HotNews Notes and four High Priority Notes
- Highest CVSS Score of New Notes is 9.0—Improper Authentication vulnerability in SAP NetWeaver AS ABAP and ABAP Platform can be used to bypass protection against external calls
- Onapsis Research Labs Collaboration—20 vulnerabilities detected, patched with six SAP Security Notes
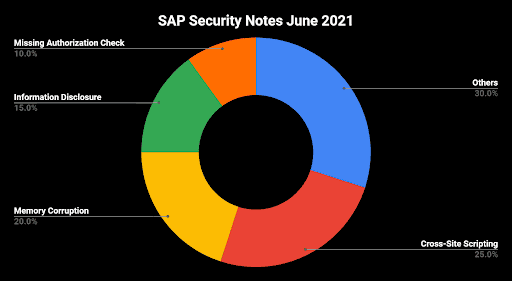
SAP has published 20 new and updated Security Notes on its June Patch Day. This number includes two HotNews Notes and four High Priority Notes.
Fortunately, one of the two HotNews Notes is just a minor update on SAP Security Note #3040210, originally published on SAP’s April Patch Day. The note fixes a serious Remote Code Execution vulnerability in the Rules Engine of SAP Commerce. The new version of that note only contains an updated link on a FAQ document.
The really remarkable aspect of this Patch Day is the fact that three of the four High Priority Notes affect SAP kernel processes that exist since the beginning of the SAP R/3 era and they can be seen as the heart of an SAP NetWeaver AS ABAP and ABAP Platform.
Most Critical Vulnerability in SAP NetWeaver AS ABAP and ABAP Platform
SAP has patched a serious Improper Authentication vulnerability. An ABAP server could not 100% correctly identify, if communication via RFC or HTTP is between the application servers of the same SAP system or with servers outside the same system.
This enabled a malicious user to abuse stolen credentials from an internal communication between two servers of the same system for external RFC or HTTP calls. The credential data could be used to establish an own connection between a malicious external program and the affected SAP system pretending to be an internal caller.
In a lot of cases, function modules need to be RFC enabled because some programming techniques, e.g. parallelization, require this attribute. An often used method to protect such a function module against external calls is an explicit check for the source of the call (external/internal) inside the function module (an example can be found in the last section of the next chapter). If this check does not work properly, the designated protection will fail.
SAP Security Note #3007182, tagged with a CVSS score of 9.0, provides a kernel patch and an ABAP correction to fix this issue.
Onapsis Research Labs Contributed in Solving 20(!) Vulnerabilities
As a result of the Onapsis mission in helping SAP protect its customers, the Onapsis Research Labs contributed to patching 20 vulnerabilities on June’s Patch Day. The patches are covered by six SAP Security Notes, four of them rated with High Priority.
SAP Security Note #3053066, tagged with a CVSS score of 8.6, patches a Missing XML Validation vulnerability in SAP NetWeaver AS Java.
Communication profiles are entities that contain policies with which the communication between a provider and a consumer system has to comply. Knowing the policies to a given provider system, a technical administrator specifies a collection of settings such as transport settings, Web Services Reliable Messaging (WS/RM) settings, and authentication level in the communication profile.
SAP NetWeaver Administrator allows the transfer of such a communication profile from one system to another by providing appropriate export and import capabilities. The Onapsis Research Labs has detected that the import process doesn’t sufficiently validate the content of the imported XML file. The lack of validation would allow a user who is authenticated as an administrator over a network to abuse the import feature by submitting a specially crafted XML file containing malicious content. Processing such content by the system can fully compromise system confidentiality by allowing the attacker to read any file on the filesystem or fully compromise the system’s availability by causing the system to crash.
The Onapsis Research Labs also detected a series of memory corruption vulnerabilities in core processes of an SAP NetWeaver AS ABAP and ABAP Platform.
The SAP Security Notes #3021197, #3020209, and #3020104, all tagged with a CVSS score of 7.5, patch 11 vulnerabilities in total. These vulnerabilities can cause memory corruptions in: work processes, dispatcher process, SAP Gateway process and Enqueue process.
The vulnerabilities allow an unauthenticated attacker without specific knowledge of the system to send specially crafted packets over a network which will trigger an internal error in the system causing the service to crash and render the system partially or completely unavailable.
Similar vulnerabilities were found by our Research team in SAP Internet Graphics Server (IGS). SAP IGS is a widely-used, server-based engine for generating graphical and non-graphical content based on data from an SAP system or an external system. An integral part of its architecture are different interpreters responsible for the semantic processing of the received data. The appropriate interpreter is selected by a portwatcher and depends on the basis of the requested type of information (ex: chart, map, zip).
SAP Security Note #3021050, tagged with a CVSS score of 5.9, patches seven vulnerabilities in the portwatcher and in several interpreters. The patch contains additional input validation of incoming IGS requests preventing an attacker from sending malicious requests that could trigger an internal memory corruption error in the system causing the system to crash and rendering it unavailable.
The reason for the lower CVSS rating of this vulnerability compared to the previously described vulnerabilities is the fact that the complexity of an exploit is considered to be higher in the SAP IGS scenario.
Last but not least, our Research Labs (to be honest – the author of this article :)) also detected a Missing Authorization vulnerability in SAP NetWeaver AS ABAP and ABAP Platform. SAP Security Note #3002517, tagged with a CVSS score of 6.3, patches a lack of appropriate authorization checks in an RFC enabled function module of SAP Records Management. A low privileged attacker was able to start arbitrary reports over the network. SAP has fixed the issue by only allowing system internal RFC calls of the affected function module (refer to previous chapter) and by adding an additional authorization check for the submitted report.
Summary and Conclusions
SAP’s June Patch Day has shown that it would be careless to not expect security issues in software components that already exist for decades. In particular, the major kernel processes are often subject to extensions and adjustments to meet new technical requirements so that they cannot be considered as “rock solid” just because of their age. But, even for components not changing that frequently, a secure status cannot be taken for granted. An example for that is SAP IGS. While there were no new vulnerabilities reported on SAP IGS in the last 30 months, the Onapsis Research Labs found seven issues immediately when starting their analysis.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
