SAP Security Notes January 2020: ICM Services at Risk of Denial of Service
Highlights of January SAP Security Notes analysis include:
- New “SAP Security year” starts like old one has ended – very “calm”—Only 12 new SAP Security Notes, 1 High Priority Note, 10 of Medium Priority and 1 with Low Priority
- Onapsis reported threat fixed—Denial-of-Service(DOS) vulnerability in SAP ICM eliminated
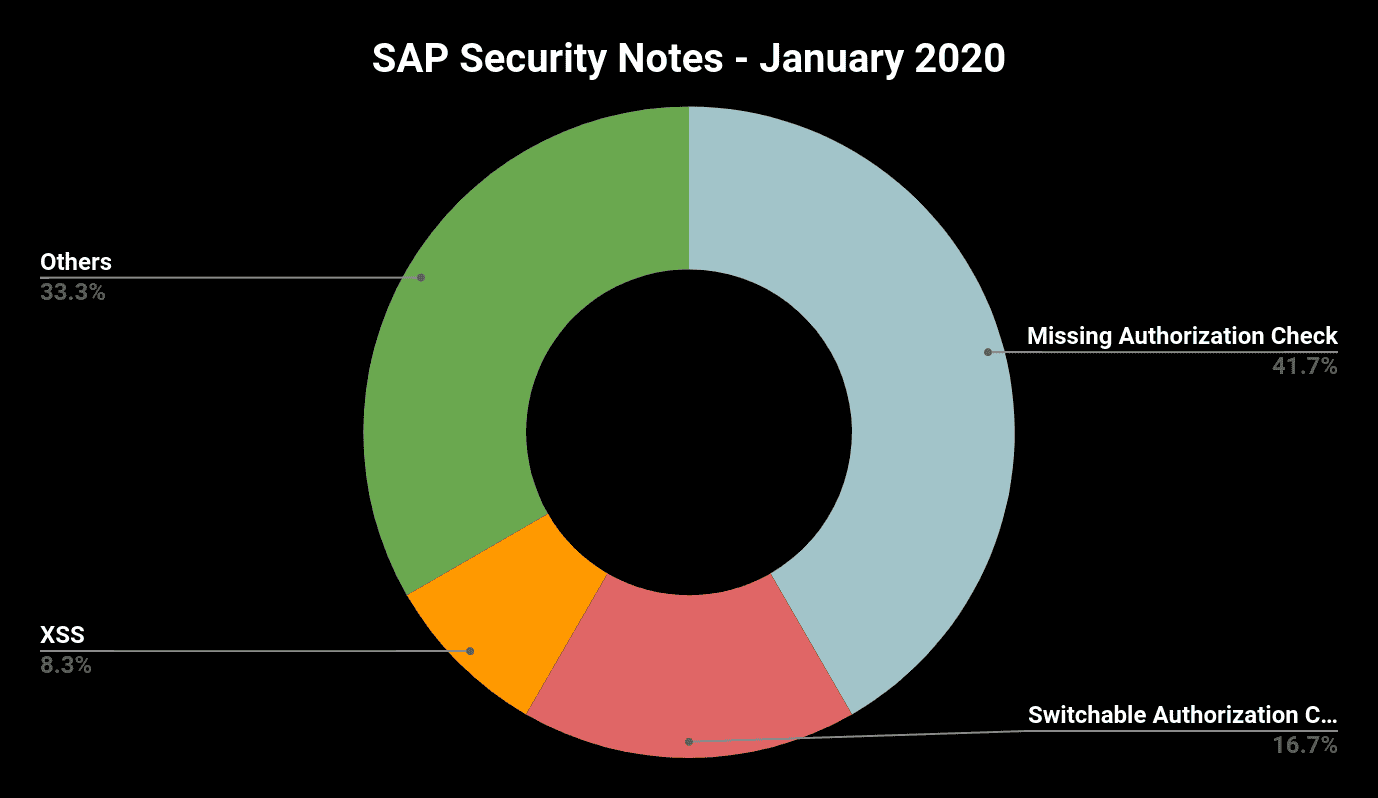
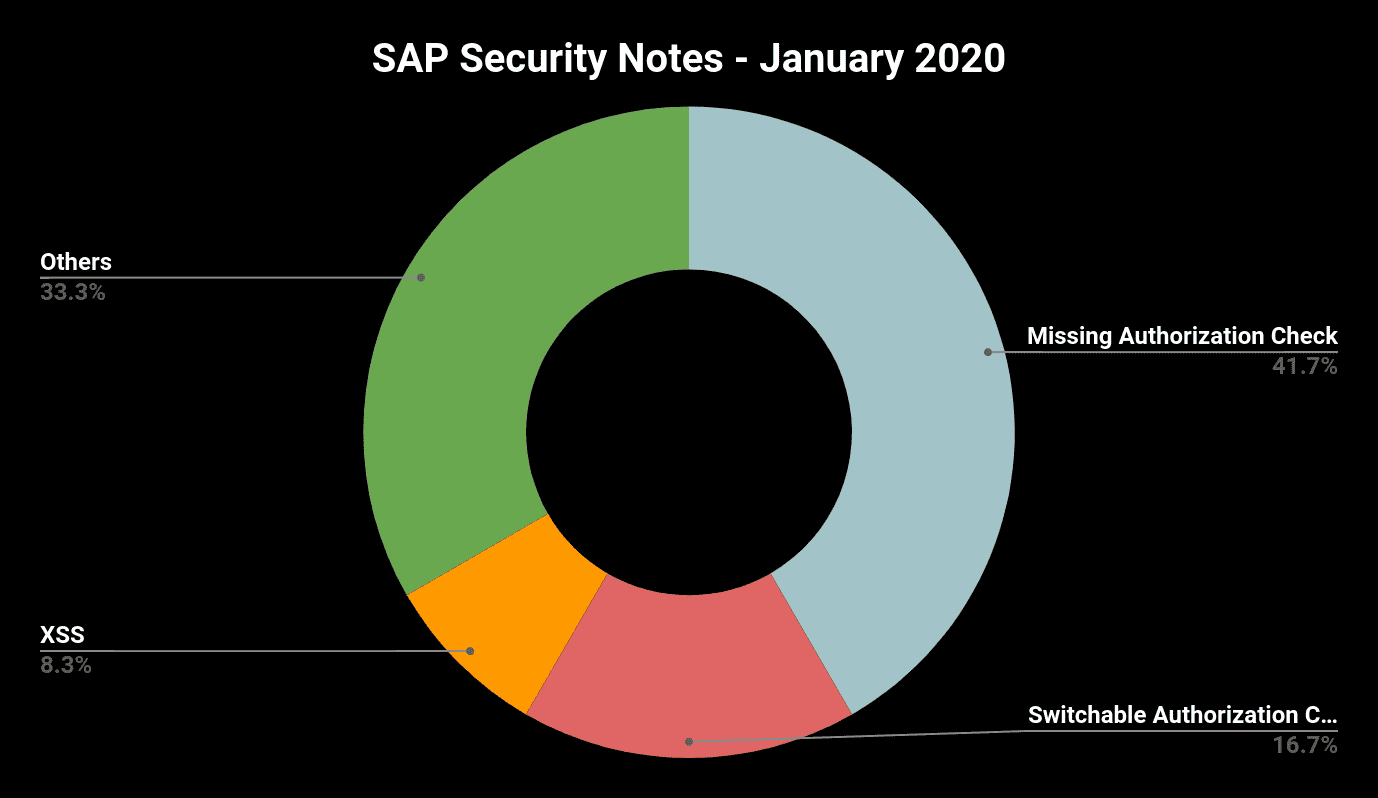
- “Missing Authorization Check” is January’s top scorer—58%(!) of the released notes are caused by missing authorization checks
2020 has started like 2019 has ended—a relatively small number of new SAP Security Notes has been released in January, only one of them tagged as “High Priority”. This time the Onapsis Research Labs could participate again in making SAP systems more secure through reporting a Denial-of-Service vulnerability, now fixed by SAP.
Denial-of-Service vulnerability fixed in SAP NetWeaver Internet Communication Manager (ICM)
In September 2019, the Onapsis Research Labs detected a DOS vulnerability that affects all components communicating with the SAP system via Internet Communication Manager(ICM) (e.g. all SAP Fiori applications). An attacker can send a specially crafted packet to the IIOP or P4 service in order to cause a buffer overflow and thus crashing the ICM process.
So the impact on the availability of all web-based SAP applications is posed at high risk. The reason for rating this vulnerability “only” with CVSS value 5.9 is caused by the fact that an exploit requires the parameter rdisp/TRACE to be set to a value higher than 1. This value is not part of the default configuration and is normally only set in case of tracing the cause of an issue. That’s why we tagged with the vendor Attack Complexity (AC) in CVSS vector as High. Nevertheless, if you have the tracing in the vulnerable configuration value, attack complexity is not high and this would raise the CVSS to 7.5. That’s why CVSS score is a good value as a reference but needs to be analyzed by every company and do not be confused with risk value.
On this Security Patch Day SAP has fixed the vulnerability and provides a kernel patch so that all customers can now eliminate it from their systems.
Multiple Security Issues in SAP Enterprise Asset Management, Add-On for MRO 4.0 by HCL for SAP S/4HANA 1809
SAP has released one High Priority Note (#2871877) between today and last Security Patch Day that provides multiple corrections in different areas of the SAP EAM add-on. Different kinds of vulnerabilities are covered in various components of the add-on, e.g. Missing Authorization Check vulnerabilities in several Workbenches of MRO (CVSS rated with 8.3), and Directory Traversal vulnerabilities allowing attackers to read, overwrite, delete, or corrupt arbitrary files on the remote server (CVSS rated 7.2). Pay attention: the corrections are provided as an SAP Transport File!
Januar Patch Day Once More Dominated by Missing Authorization Check Vulnerabilities
This month 7 of 12 notes were initiated by missing authorization checks (2 of them fixed through the introduction of new switchable authorization checks). 3 of the 7 notes fixes the absence of explicit application-specific authorization checks in RFC-enabled function modules. This time, SAP Leasing (SAP Security Notes #2495462 and #2865348) and a third party vendor software component in SAP Solution Manager (#2845401) are affected. Missing explicit authorization checks in RFC-enabled function modules is still one of the most detected vulnerabilities especially in custom code. Relying only on implicit checks on authorization object S_RFC is very dangerous as authorizations on this object are defined very often too generously. They allow the access either to all RFC-enabled function modules or to the function modules of a complete function group. The later situation is often caused by the fact that in earlier SAP NetWeaver versions, object S_RFC did not provide the possibility to assign individual function modules and customers missed to introduce a more granular authorization concept afterwards.
Another interesting note is SAP Security Note #2863397, titled “Missing Authorization Check in Automated Note Search Tool (SAP_BASIS)”. SAP has re-introduced an authorization check in the Automated Note Search Tool (ANST) that some customers could have removed years ago due to a problem in case a user does not have the required authorizations (SAP Note #2253694 released in 2015!). This is a good lesson for customers: it is never a good idea to solve an exception handling problem after a failed authorization check by just removing or disabling the authorization check. Security is sometimes the enemy of usability, but it is always recommended to spend time adding the required authorizations instead of deleting them.
Summary & Conclusions
The new year starts very calm and thus giving customers the opportunity to finally check if they have setup the connection to the new SAP Backbone correctly and if transaction SNOTE is now prepared for downloading digitally signed SAP Notes. This months’ SAP Security Notes reflect once more the typical development mistakes and should be a great motivation to cross-check also the custom code.
The Onapsis Research Labs is already working to update The Onapsis Platform to incorporate these newly published vulnerabilities into the product so that our customers can check missing notes during their security assessments. We are also working to share with you, as we’ve been doing for a few years, a summary of what happened with SAP Security Notes during 2019. Meantime, let’s start the new year with security as a priority and ensure you update your systems with January patches
