SAP Security Notes December 2019: New Supported Chromium Version for SAP Business Client is the Only HotNews
Highlights of December SAP Security Notes analysis include:
- “Calm” December on SAP Security Front—Only one HotNews Note and 12 Medium Priority Notes released
- Expected Update on HotNews Note #2622660—New supported Chromium version Chrome 78.0.3904.70 still does not cover important zero-day patches
- New MDM update no longer supports SSLv3—Another step towards secure communication in SAP
Characterizing SAP’s December Patch Day as “calm” should not be misinterpreted. While the number of 12 Medium Priority Notes (plus one update on a HotNews Note) suggests that there is no urgent need to implement the corresponding patches, each SAP customer should reflect on the priorities and CVSS ratings applied by SAP in more detail. SAP Security Note #2741937, titled “SQL Injection Vulnerability in Central Finance CO” is a good example of this recommendation. The CVSS rating of 6.5 can be debated, given the fact that the vulnerability allows to “execute admin-level operations on database.” So, rating the possible impact on the system’s integrity and availability with “None” is at least a “courageous” decision.
Update on HotNews Note #2622660
SAP has released the expected update on the supported Google Chromium version for SAP Business Client. Less expected was the fact that the supported version still doesn’t cover the CVE-2019-13720 and CVE-2019-13721 vulnerabilities published by Google six weeks ago. While these vulnerabilities more represent a direct risk for the user’s client PC than for an SAP system, users are exposed to unnecessary risk here by forcing them to stay on an insecure Chromium version. In addition, given the fact that CVE-2019-13720 was already exploited and SAP systems might be impacted indirectly through infected client PCs connected to the same network, the next update on this note will be more than welcome.
MDM supports TLSv1.2 now with no option to fallback to SSL
At first glance, SAP Security Note #2504979, titled “Upgrade SSL Support to TLSv1.2” sounds like a simple notification for SAP MDM customers that communication security in this area was improved. But in fact, this is important news for everyone responsible for securing network communication.
If an SAP application does not restrict the SSL/TSL versions (and cipher suites) that it provides for the communication with a client, attackers can take advantage of a specific feature of modern clients. When initiating a handshake with the server, the clients will offer the “most secure” protocol that they support. If the connection fails, they will automatically retry again with a “more insecure” protocol until the handshake is successful with the server. Attackers can force these clients to automatically downgrade to an SSL/TLS version that supports cipher suites with algorithms that are known for weak security and vulnerabilities. This type of attack is known as a POODLE attack. More information about POODLE can be found here.
As protocol version SSLv3 (and meanwhile also TLS 1.0 and TLS 1.1) was broken already years ago, every new SAP component supporting TLS 1.2 and denying SSL protocols is an important step towards secure communication within SAP. While TLS 1.2 is a highly recommended standard today, interoperability with legacy systems often forces security administrators to still allow SSLv3 in SAP environments. SAP Note #2384290 provides meaningful information about enforcing TLS 1.2 in an SAP environment, including prerequisite on some often used third-party software components.
For more information about TLS, read this recent Onapsis blog: TLS: Much more than a Compliance Requirement.
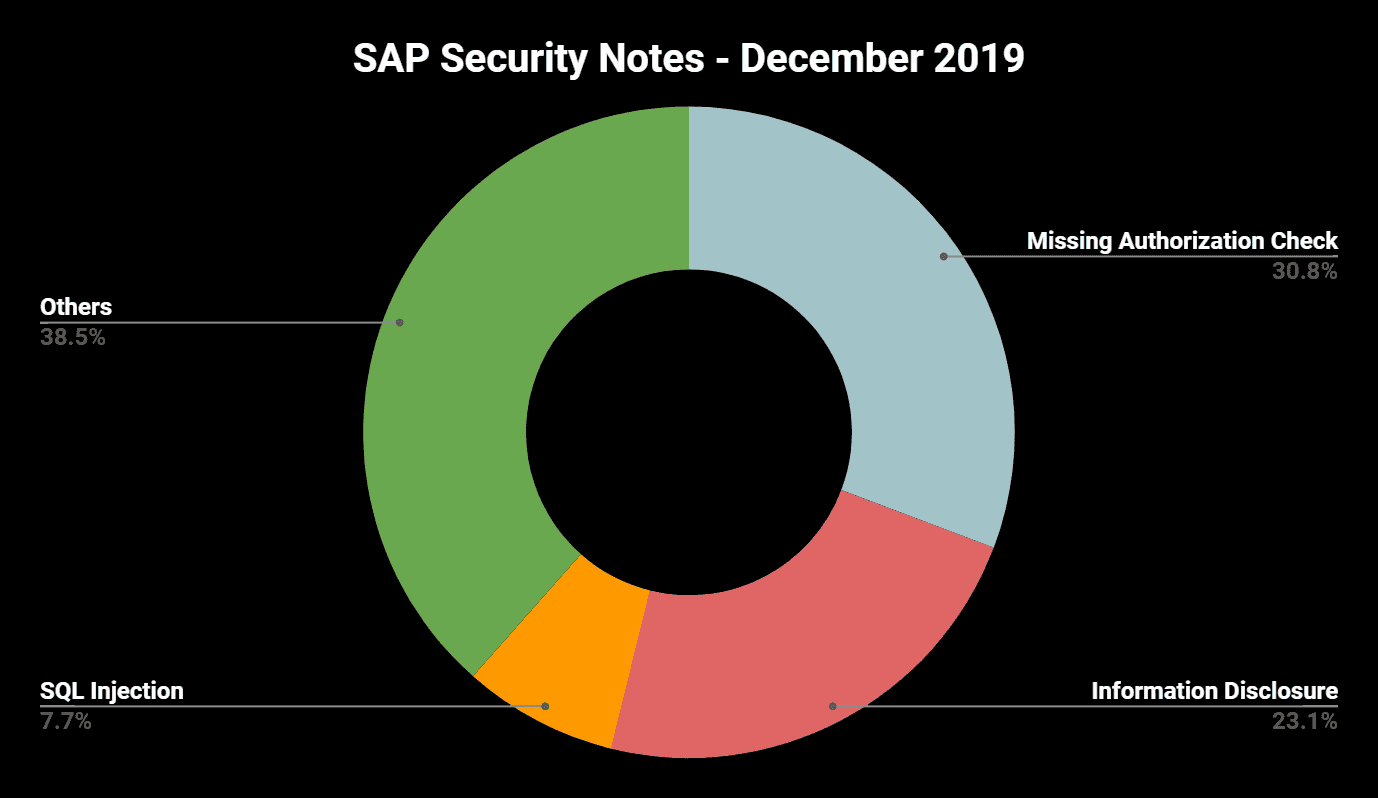
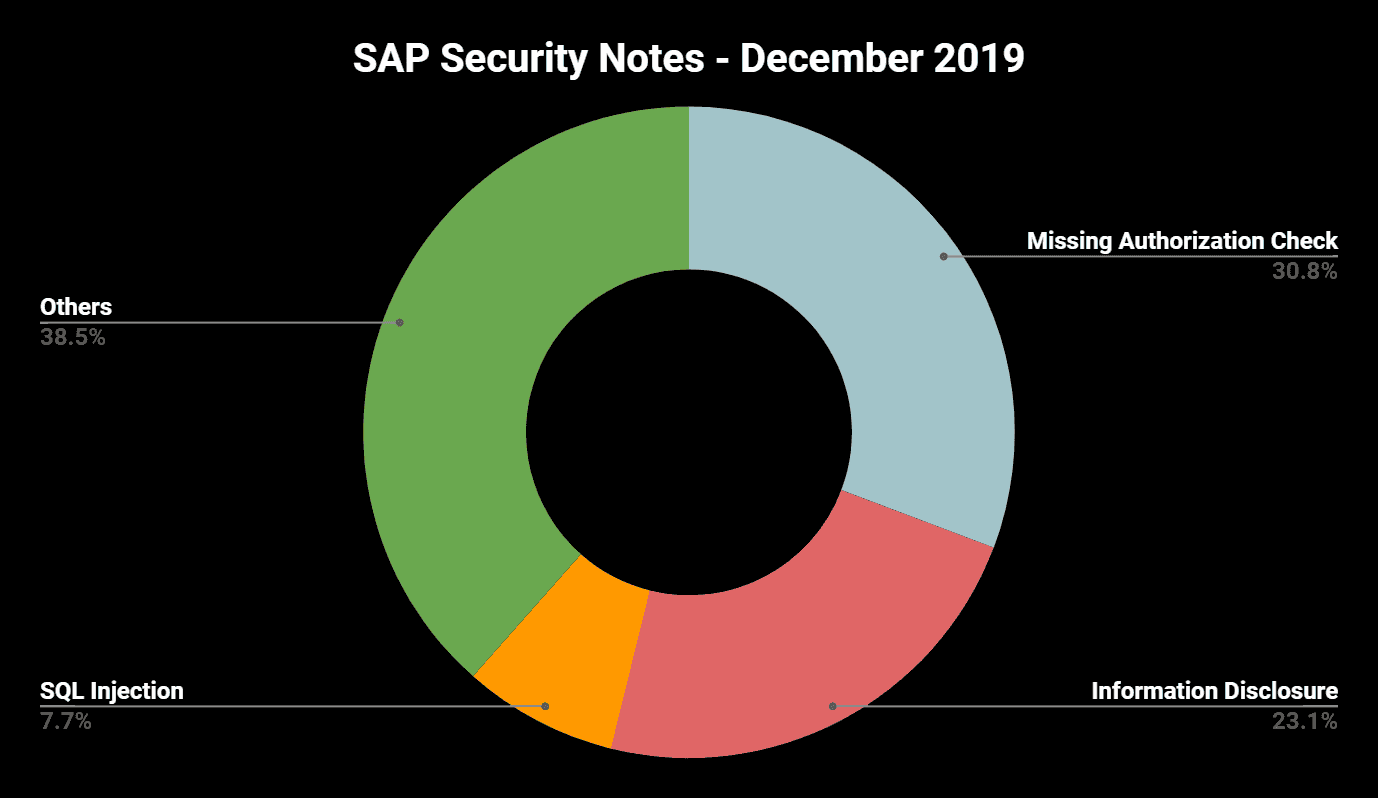
“Missing Authorization Check” once again the number one vulnerability
This month includes four SAP Security Notes covering Missing Authorization Check vulnerabilities in ABAP components. The result of the SAP December Patch Day is also an important reference for customer development projects. Typical mistakes that can be found here are:
- Missing explicit AUTHORITY-CHECK in remote-enabled function modules
- Missing AUTHORITY-CHECK before CALL TRANSACTION
- Missing explicit AUTHORITY-CHECK in reports
- Missing or incomplete exception handling after failed authorization checks
- Incomplete authorization checks (inadequate checks on DUMMY)
Summary & Conclusions
With only one updated HotNews Note and 12 Medium Priority Notes (eight new notes and four updated notes), SAP’s December Patch Day may be seen as less impactful. Nevertheless, when looking into details, the provided corrections solve security issues that might be more critical than their priority and CVSS rating might indicate at first glance. These “calm” Patch Days should also be used to cross-check own developments with regard to the described vulnerabilities.
The Onapsis Research Labs is already working to update The Onapsis Platform to incorporate these newly published vulnerabilities into the product so that our customers can check missing notes during their security assessments.
For more information about the latest SAP security issues and to stay in tune with our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
