SAP Security Notes 2016: A Year in Review
Since its foundation, the Onapsis Research Labs have been actively helping SAP improve its security by researching and reporting system vulnerabilities. On the second Tuesday of each month, the Onapsis Research Labs publishes a detailed analysis of the latest SAP security notes. This helps to better assist our customers secure their SAP systems from the latest threats, and helps to ensure that our products are designed to continuously detect new vulnerabilities. This week, right before first analysis of 2017 SAP Security notes, we’d like to share with you a full review of what happened in 2016 regarding SAP security. Included in this year in review is a new infographic we put together to summarize the major areas of focus 2016 saw. You can download it here, or you can keep reading along for a more detailed exploration of the information detailed in the infographic.
Summary – Historical Overview
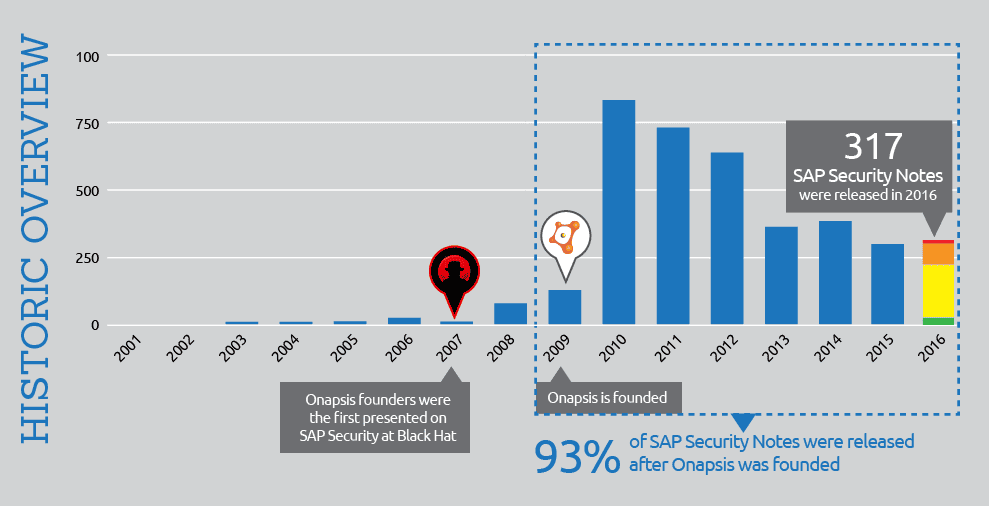
This year, SAP released a total of 317 security notes. Compared to the 302 notes released in 2015, this is only a 4.3% growth rate which does not represent any significant change. The graph below depicts the number of patches published over the last four years: 
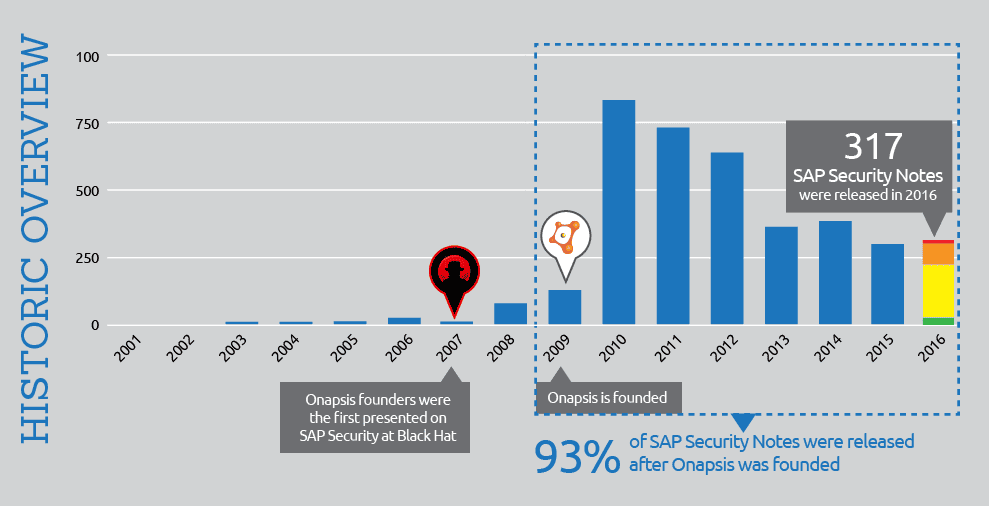
As shown in the graph, there’s a first spike in 2008, right after Onapsis first presented on vulnerabilities found in RFC protocol implementation and library at the 2007 Black Hat Conference. During this time, SAP security was a “dark world” and little information was available about vulnerabilities and mitigation information on the internet. This is why there was such a low quantity of security notes released up to that year. Over the next two years (2008 and 2009), there was an increase in the number of Security patches which surpassed the number or security notes released from 2001 to 2007. It is also interesting to highlight that in September of 2009, just prior to the exponential growth of SAP Security Notes in 2010 Onapsis was formally founded. So to summarize, 16 years of SAP security notes can be easily grouped in three phases:
- The first eight years (2001 to 2008) marked the genesis of SAP Security, no more than 100 SAP security notes per year were published during this time.
- The following four years (2009 to 2012) marked the explosion. SAP publishes over ‘100’ security notes in 2009, and in 2010 published over 800 security notes. During these four years SAP published 15x more security notes than the previous eight years combined.
- Finally, the number of security notes published over the last four years has been more stable, averaging ~340 SAP Security Notes per year and without significant differences.
Automatic vs. Manual: Installing 2016 Security Notes
Another interesting thing to analyze is the method in which a security note can be installed. Unlike other vendors, not all security notes in SAP have a direct impact on security after installation. Some notes require manual steps to be performed to ensure that the vulnerability was fully patched. According to the type of installation required, we can classify SAP security notes into two groups: automatic and manual. The automatic notes don’t need any additional interaction for the installation to take effect. This group represented 71% of security notes released in 2016. However, despite the ease of installation, this does not mean that automatic notes are any less critical than manual ones. For example, the security note with the highest CVSS score of 2016 was an automatic note; 1682613 “Missing authorization check in core service” with a CVSS base score of 10. On the other hand, the manual notes require some additional and manual steps that must be followed to accomplish the installation. This group represents 29% of the security notes released in 2016. It’s interesting to note that the highest scoring non-automatic security note score only has a CVSS of 5.5: 2282338; “SAP Download Manager Password Weak Encryption”. In theory, it should be a good sign that the more critical vulnerabilities can be patched with automatic notes. This is mostly true as there are several security notes where SAP does not specify a CVSS Score, so these notes could potentially be critical in nature. But for sure we can say that for all of the vulnerabilities SAP has published with a CVSS score, the most critical ones can be installed automatically without any manual steps.
Top 5: Vulnerability Types of the Year
There are no surprises in this area. The below graph summarizes the different types of vulnerabilities fixed in 2016:
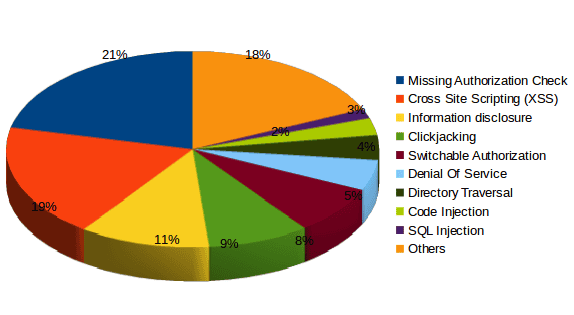
As expected, Missing Authority Check, Cross-Site Scripting and Information Disclosure are the most common vulnerability types of 2016.
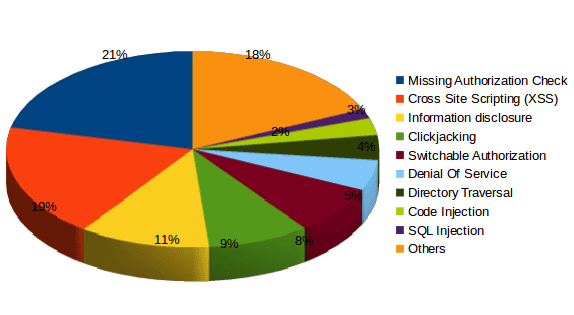
Nevertheless, there are some unexpected bugs in the most common ones. Let’s take a look to the Top 5:
- 1. Missing Authorization Check: Despite these vulnerabilities being traditional in terms of quantity, 2 of these notes were tagged as ‘Hot News’ items this year. The last Hot News that fixed a Missing Authorization Check had been published in 2013.
- 2. Cross-Site Scripting (XSS): XSS vulnerabilities are one of the most frequent types of vulnerabilities in the history of SAP Security Notes, and this year was no the exception.
- 3. Information Disclosure: In addition to XSS and Missing Authorization Check, this type of vulnerability is always present. Since 2010, more than 30 SAP security notes per year are released to Information Disclosure vulnerabilities.
- 4. Clickjacking: Surprisingly, this type of bug appears in the Top 5 this year. 29 security notes have been published regarding to Clickjacking so far with 28 of them released in 2016.
- 5. Switchable Authorization Check: This type of vulnerability relates to authorization checks that are fixed but have to be explicitly enabled. 41% of SAP Security Notes released in 2016 were related to Switchable Authorization Check was released in 2016, totaling 61 Notes.
Onapsis Research Labs Contribution
We have always worked to help SAP protect their customers, and a large part of this job is to find vulnerabilities and responsibly report them to vendors in order to help them patch their products before attackers can abuse it. This year, 50 vulnerabilities reported by the Onapsis Research Labs were fixed by SAP. These patches were grouped into 23 SAP Security Notes, which can be split up based on the affected platform. Most of the issues reported by our researchers were rated ‘Medium’ and ‘High’ priority, which means that they must be corrected quickly:
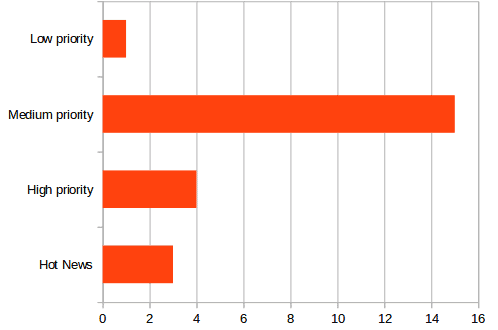
It is interesting to remark that 3 of 9 ‘Hot News’ items released this year were reported by Onapsis Research Labs. All three are related to code injection attacks:
- OS Command Injection Vulnerability in SCTC_* Function Modules (2260344):
- CVSS v3 Base Score: 9.0.
- Full details here: Analyzing SAP Security Notes March 2016.
- OS Command Injection vulnerability in Report for Terminology Export (2357141) and Code Injection vulnerability in Text Conversion (2371726):
- CVSS v3 Base Score for both: 9.0.
- Full details here: SAP Security Notes November 2016 – The Return of OS Command Injection.
Congratulations to all our security researchers that have collaborated this year to continue improving the state of SAP security.
Conclusion: Time of Stability?
The overview of SAP security notes from 2016 leads us to a simple question: are we currently experiencing the time of stability? And if so, does it mean maturity? It seems that cybersecurity for SAP is beginning to enter a more stable era, not only because of the fewer amount of bugs that are corrected, but also because SAP is taking care of more now compared to five years ago (more than 500 SAP Security Notes per year), such as clickjacking or switchable authorization checks. This is good news for you! Now there are more notes and more ways to keep your SAP infrastructure secure. However, in order to do so, you must take care of it and make remediation of SAP vulnerabilities a core part of your security strategy. One of the biggest news stories of 2016 regarding business-critical applications security was the DHS US-CERT Alert on SAP business applications. This marked the first-ever CERT Alert for SAP and warned against an SAP vulnerability that was patched by SAP over five years ago. It is extremely important to keep your systems up to date in order to ensure that your SAP landscape is secure. Remember, our new infographic on 2016 SAP Security Notes can be downloaded here: https://onapsis.com/resources/infographics. Stay tuned, for our first patch Tuesday of 2017 coming up next week!
