SAP Security Notes February ‘19: Several Critical Onapsis Reported Bugs Patched
It’s the second Tuesday of the month and, guess what, SAP has released the second set of Security Notes for the year. As with every month, we have provided an analysis of this month’s Patch Day. Today, SAP published 16 new SAP Security Notes, including one that is the first HotNews affecting SAP HANA XSA (extended application services, advanced model). Also included are four other vulnerabilities reported by the Onapsis Research Labs:
- One High Priority note affecting SLDREG component, present in several products
- Two of four Onapsis reported notes represent half of the four vulnerabilities with the highest CVSS score
- One of these two is an update for a previously published note based off an Onapsis report
- Another two vulnerabilities, both tagged as Medium Priority, affect another mobile platform (as we reported last month) and SAP BusinessObjects, where we have helped SAP patch another four bugs (in three SAP Security Notes) in the last year
As mentioned, one of the two SAP Security Notes tagged as HotNews (#2742027) affects SAP HANA XSA (the other one is #2622660 that is regularly updated with Chromium security updates and was explained in a previous blog post). It is a classic Missing Authorization Check that may allow an attacker not only to read/modify/delete sensitive information, but also to gain high-privileged functionalities. It affects XS Advanced selected versions in both SAP HANA 1 and SAP HANA 2 and can be patched by upgrading the XS Advanced component. If XSA cannot be updated in the short term, SAP also details a workaround to avoid further attacks, by disabling the affected component if it’s not used (check SAP Launchpad for details).
SAP Updates High Priority Note Based on Onapsis Reports
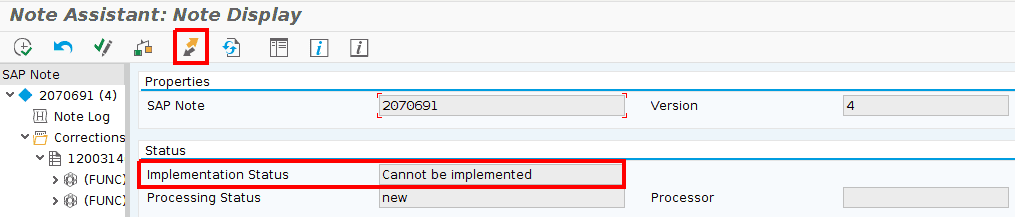
SAP Security Note #2070691 was first released in 2014 and this month was re-released thanks to the collaborative effort of our researchers and SAP. This note, tagged with CVSS v3.0 Base Score 7.7/10 patches two functions that could lead an attacker to get information stored in files on the operating system level on the database server.
The previous version of this note affected ABAP systems that have installed the software component ST-PI, which is an add-on that contains the Service Data Control Center (SDCCN), with Support Package (SP) 0. If you had tried to install it having SP higher than 0, you would have seen that the note was shown as Cannot be implemented in the SNOTE transaction code:
XXE in SLDREG Affecting Several Products
SAP Security Note #2729710, tagged as High Priority, fixes a serious vulnerability reported by the Onapsis Research Labs. The security bug, titled “XML External Entity (XXE) vulnerability in SLD Registration of ABAP Platform,” was found during our research. The vulnerability affects a kernel component present in every SAP system.
SLD Registration (SLDREG) is a binary which is used for sending information on the SAP system to the configured Solution Manager (SOLMAN). It is stored in the Operating System (OS) and researchers discovered that it can be remotely executed. The importance of this bug is that, the SLDREG binary is present in every SAP platform, such as ABAP, JAVA, etc. Therefore, there may be other places to successfully exploit it than the one discovered by Onapsis researchers.
Although this endpoint needs the credentials of the lm_service user, a user with access to them will be able to use this service. By abusing this vulnerability an attacker would be able to send a specially crafted XML payload.
The reason why this vulnerability is critical is because an attacker may compromise the system and read any file of the OS (i.e. content of the file /etc/passwd) as well as perform a Denial of Service (DoS) against the SAP system.
The vulnerability was fixed by the vendor and published with a high CVSS v3.0 Base Score 8.6/10. The impact of this security bug is high in the security values for Confidentiality and, what’s more, Availability. The latter is affected because, although the vulnerability seems to only allow files to be read, something worthy of attention is that the XML External Entity (XXE) vulnerability, in general, contains something called an XML Entity Bomb. This attack is a piece of XML code, syntactically valid and correct, that could store entries to references which refer to other references (generating a loop) and that nested data entities start growing exponentially and can result in a DoS.
This bug, found by Onapsis researchers Nahuel D. Sanchez, is part of their presentation next March, in Germany, at the upcoming Troopers Conference. They will provide a talk titled, “Dark Clouds ahead: Attacking a Cloud Foundry Implementation,” showing how through combining several vulnerabilities, even ones that are not tagged as HotNews, attackers can get critical access to the system.
However, the Onapsis Research Labs has found that the bug was also present in systems with higher SP. In fact, systems with ST-PI with SP lower than 11 are vulnerable to this information disclosure. Therefore, SAP released today an updated version of this note offering the patch for all the vulnerable versions. Now, to patch your system you could enter that note in the Note Assistant, click on the ‘Download Latest Version of SAP Note’ icon and it will appear as Can be implemented. Then, you implement the note and problem solved!
Other Notes Reported by Onapsis Research Labs Affecting SAP Business One and SAP BusinessObjects
As mentioned before, there are two vulnerabilities that were reported by our researchers and properly fixed this month, both of them tagged as Medium Priority and with CVSS v3.0 Base Score of 6.1/10.
The first one is another patch based on Yvan Genuer’s research on SAP Mobile Applications, that lead to the first patches released last month. Today, SAP Security Note #2723878 solves an Information Disclosure in SAP Business One Mobile app for Android. The bug affects only Android applications and can be solved by upgrading to latest version through Google Play.
The last note reported by the Onapsis Research Labs is a finding by Gaston Traberg, who has discovered several vulnerabilities in SAP BusinessObjects. This one, SAP Security Note #2638175 is a Cross-Site Scripting (XSS) vulnerability in the SAP BusinessObjects Fiori Launchpad. It is a classic XSS bug where an attacker may execute code in the client if a potential victim accesses a specially crafted URL. Onapsis Security Platform customers have received coverage for BusinessObjects since the launch of version 2.0 that came out last year. This includes checking for missing notes like the one published this month.
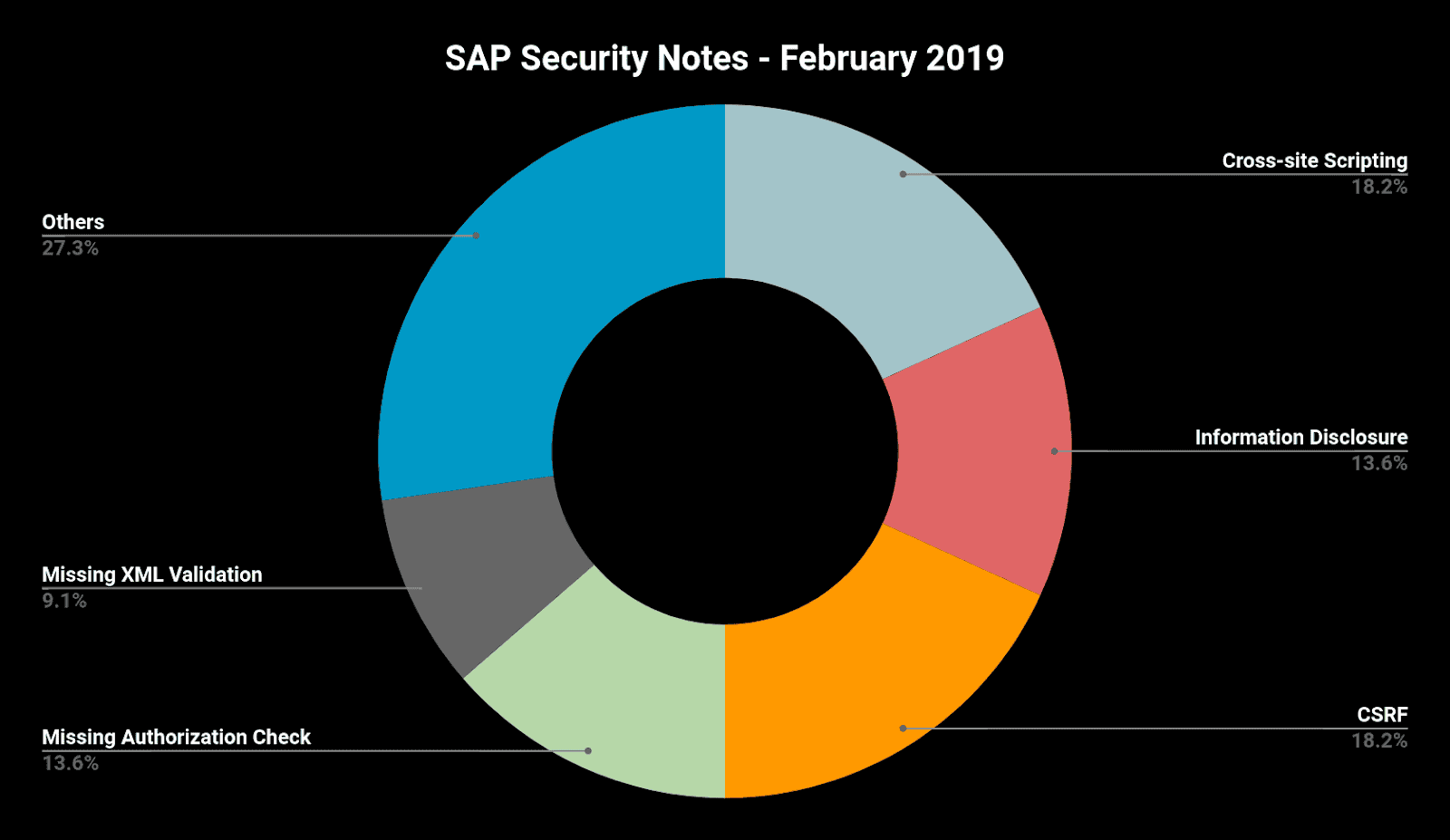
Below is a summary of the type of vulnerabilities that were fixed this month, including not only 16 SAP Security Notes, but another six that were published in late January, after that month’s Security Notes Patch Day.
As you may see in the SAP acknowledgment to Security Researchers, Onapsis is the only company with several researchers on this page. Five of our team members have been recognized this month based of their findings and reports. As always, we are working to update the Onapsis Security Platform to incorporate these newly published vulnerabilities to allow our customers to check whether their systems are up to date with the latest SAP Security Notes. Follow us on Twitter to keep tracking ERP Security News and continue to read our ERP security blog.
