Oracle July CPU Analysis: Onapsis helps patch critical vulnerability in E-business Suite
As a security vendor and Research Labs with the goal of protecting our customer’s business-critical applications we also have the continuous balance of proactively informing the community about emerging threats affecting their critical applications. A big part of this is our continuous work with vendors to help them secure vulnerabilities in their software. Today, for the third time, the July 2017 Oracle Critical Patch Update breaks a record on number of patched bugs with 308 vulnerabilities solved. In addition to that, Onapsis reported half of the patched vulnerabilities in E-Business Suite (11 of 22) including a high risk vulnerability that allows a remote unauthenticated attacker to download documents from the database.
Because of the criticality of this specific bug, we released a dedicated Threat Report to provide the community with a deeper understanding of the potential business impact. In today’s blogpost, we will explain each additional vulnerability reported by Onapsis Research Labs, the business impact and how important is to implement the patch from the Critical Patch Update report.
Threat Report: Unauthorized Exfiltration of Business Documents
In April 2017, Onapsis Research Labs discovered and reported to Oracle numerous vulnerabilities affecting Oracle E-Business Suite applications. One of these vulnerabilities is a critical Information Disclosure vulnerability (CVE-2017-10244). The vulnerability allows attackers to exfiltrate sensitive business data without requiring a valid user account in the system.
The affected component enables users to download documents that were attached by users across the different modules of E-Business Suite, since the system was implemented. Documents could range in format, potentially being text files (.DOC), spreadsheets (.XLS), PDF or any other type of file.
This threat report aims to help Oracle EBS customers understand and protect their systems from this critical vulnerability. It is highly recommended to fix it as soon as possible, since a remote unauthenticated attacker could access arbitrary and confidential documents stored in the system.
An attacker can download documents without going through any authentication process in the system. This is one of the main contributing factors to the high risk of the bug, considering that the affected component usually stores sensitive information from the company such as Invoices, HR Candidate’s resumes, Design Documents, Customer Information, Financial Reports and potentially could even contain PII information.
All supported versions of Oracle E-Business Suite are affected: 12.1.3, 12.2.3, 12.2.4, 12.2.5 and 12.2.6. Any customer running a vulnerable version and not having the patch applied will be exposed to this attack.
Finally, depending on the industry, the exposure of these documents could lead to costly compliance violations with SOX, PCI-DSS, NIST, PII and SPI Privacy Laws, to name a few.
Download the full report for more details and mitigation information regarding this vulnerability. “Understanding the Oracle E-Business Suite Unauthorized Business Data Exfiltration Vulnerability”
Vulnerabilities affecting Oracle E-Business Suite
11 of 22 patches fix vulnerabilities originally reported by the Onapsis Research Labs. Let’s go through the additional vulnerabilities, adding context and information about them.
First of all, there is a path traversal vulnerability (CVE-2017-10192) which allows an attacker to access different files from the operating system as shown in the following image:
An attacker could abuse this vulnerability to obtain information such as system configurations and use it in combination with other vulnerabilities to target the affected system.
The vulnerabilities identified by CVSs CVE-2017-10184 and CVE-2017-10186 (that actually group multiple vulnerabilities) allow unauthenticated attackers to get arbitrary operating system files. These vulnerabilities are also Path Traversal attacks.
There are also two Denial of Service vulnerabilities. CVE-2017-10108 affects OpenJDK. During the deserialization of a specially crafted object, an attacker could consume all process Heap Memory, generating an OutOfMemoryError exception. The vulnerability exists because the class implements a readObject method without sanitization. CVE-2017-10109 is similar to the previous one, but affecting a different JAVA class.
CVE-2017-10180 is a Multiple Cross Site Scripting vulnerability which solves two different bugs with the same ID. It is multiple because there is more than one parameter which could be used by an attacker to trick an already authenticated user into executing arbitrary JavaScript code. The following is an example of how an attacker could use the authenticated session to execute their JavaScript code, this is only an example but an attacker could execute more complex and damage JavaScript code.

Additionally, there are two Cross Site Scriptingvulnerabilities patched in this CPU for Oracle E-Business Suite and reported by Onapsis researchers: CVE-2017-10185 and CVE-2017-10191.
Finally, CVE-2017-10245 is an Information disclosure vulnerability in a specific Servlet, which allow unauthenticated attacker to get a configuration file called DBC which could contain technical information that an attacker could leverage during the system compromise.
CPU Business Critical Application summary
The 308 vulnerabilities released today affects 22 different Oracle products, where 64% of these product are Business Critical Applications. The following graph summarizes the Oracle Business Critical Applications affected in this CPU where the bars represent the CVSS average for each product, the number represent the count of vulnerabilities and the point represent the maximum CVSS:
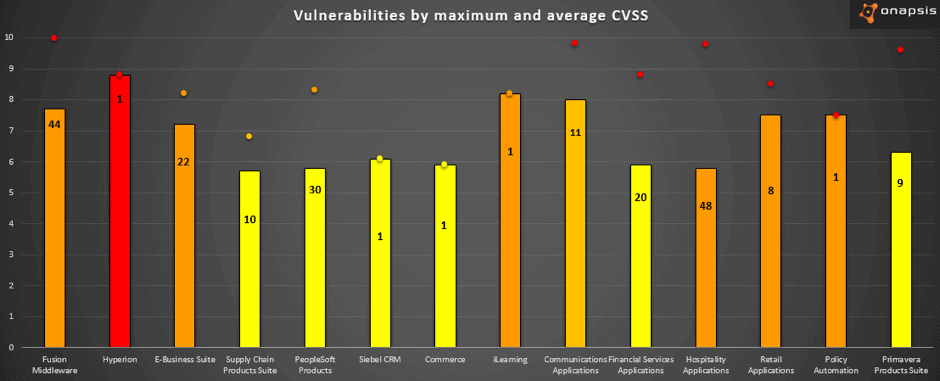
In summary: it is very clear that Oracle continues to improve the security of their products by patching hundreds of vulnerabilities each CPU with the number growing. There are different vulnerabilities which could be used by an attacker to compromise the system and get business critical information. It is crucial to update Oracle E-Business Suite with the last patch to fix all of these vulnerabilities and have the system up to date.
How to patch the system? In order to patch the system, read Oracle E-Business Suite Release 12 Critical Patch Update Knowledge Document and Implement the patch with adop or adpatch:
For each Critical Patch Update for EBS, Oracle provides two patches, one for its version 12.1 and the other for version 12.2. Customers need to download the file that matches the installed version.
Remember you can read our Threat Report and stay tuned to our blog, where we will continue to release tips and details on how you can secure your EBS systems. The next CPU is scheduled for October and as always we will publish our summary to keep you updated as soon as possible.
- p25982921_12.1.0_R12_LINUX.zip for releases 12.1
- p25982922_12.2.0_R12_LINUX.zip” for releases 12.2

