Oracle Fixes a Record of 276 Vulnerabilities in July 2016
Yesterday, Oracle released its July 2016 Oracle Critical Patch Update (CPU). This post serves to provide Oracle customers with a detailed analysis of the latest vulnerabilities affecting Oracle business critical applications.
However, this is not your average CPU as this quarter represents the largest amount of patches (276) published by Oracle – doubling the previous CPU in April 2016. This quarter’s CPU also includes 15 fixed vulnerabilities that were reported by Onapsis Research Labs. This post details those vulnerabilities and also outlines several high impact vulnerabilities providing a summary of potential business risk to business critical applications. First, we will provide a general analysis of the Critical Patch Update, and then we will specifically focus on the vulnerabilities for Oracle E-Business Suite.
July CPU: Several High Risk Vulnerabilities
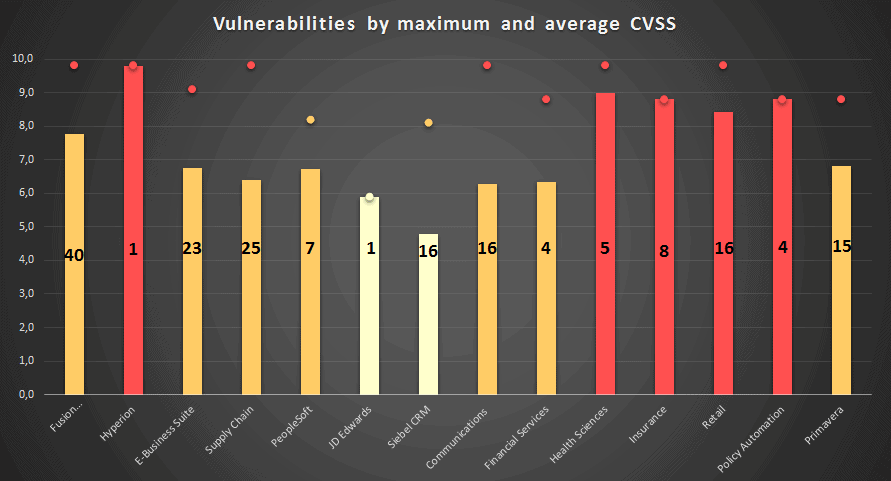
In the previous CPU, Oracle fixed 276 security issues which affected 49 different Oracle products. This is 28 more than the previous record, set in January 2016. Below, we have created a new graph that outlines how risky each published vulnerability is for Oracle Business Critical Applications. The graph was made with the following criteria:
- The bars represent the Common Vulnerability Scoring System (CVSS) average from each Oracle product group.
- The number inside the bar represents the count of vulnerabilities for the Oracle product group.
- The point represents the maximum CVSS for these Oracle product group.
- The color of the bars and the points represent the CVSS risk: Green is low, Yellow is medium, Orange is High and Red is Critical.
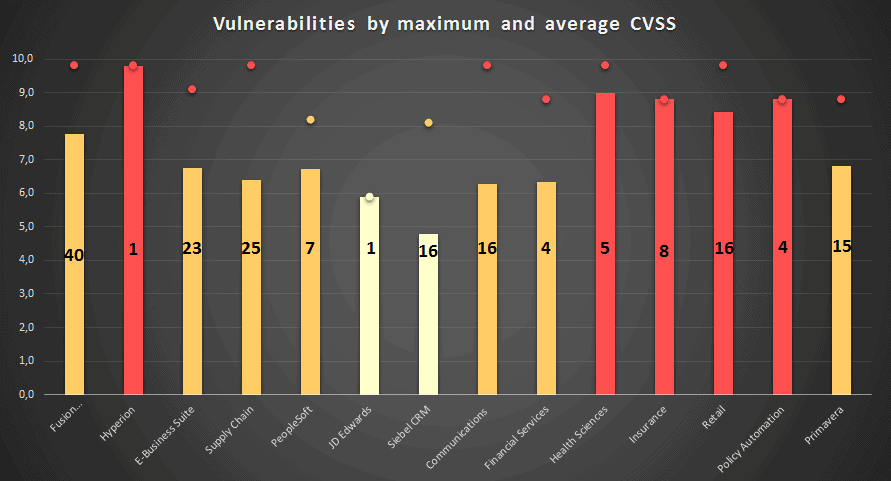
As you can see, there are not any low risk platforms (less than 4 CVSS average) and five of them average a risk value (above 8). Also, five platforms have the highest vulnerability with a CVSS 9.8
Another important metric to consider is, which of the vulnerabilities are remotely exploitable? For business critical applications, almost 60% of the vulnerabilities are remotely exploitable. This means that an attacker could potentially get access from another computer in the network.
Onapsis Research Lab Reports
As mentioned, fifteen vulnerabilities in this CPU were reported from our Onapsis Research Labs. Eleven vulnerabilities pertain to Cross Site Scripting (XSS,) and the other four relate to Open Redirect vulnerabilities. Later in this post, we will explain how Cross Site Scripting vulnerabilities work, and how to mitigate this kind of vulnerability.
All vulnerabilities reported by Onapsis relate to Oracle E-Business Suite. These were grouped in six CVEs since some of them affect the same components. Four of them have a base score of 8.2, and the others 4.7:
- CVE-2016-3532: There are seven vulnerabilities within this CVE that relate to XSS attacks. These were filed in one CVE because they pertain to the same component, but have different parameters that are not sanitized. The component involved is Oracle Advanced Inbound Telephony and the sub-component is SDK client integration.
- CVE-2016-3535: This vulnerability also relates to XSS attacks. The component involved is Oracle CRM Technical Foundation and the sub-component involved is Remote Launch.
- CVE-2016-3491: This vulnerability also relates to XSS attacks. The component involved is Oracle CRM Technical Foundation and the sub-component involved is Wireless Framework.
- CVE-2016-3536: This CVE has two additional vulnerabilities relating to Cross Site Scripting and were grouped in one CVE because they affect the same component: Oracle Marketing.
- CVE-2016-3534: This vulnerability relates to Open Redirect attacks. The component involved is Oracle Installed Base and the sub-component is Engineering Change Order.
- CVE-2016-3533: This CVE has three vulnerabilities also relating to Open Redirect attacks related to the component Oracle Knowledge Management and the sub-component Search.
How Cross Site Scripting works
As mentioned, most of the vulnerabilities reported by Onapsis are for Oracle E-Business Suite are are related to a well known attack: Cross Site Scripting (XSS). It is a web vulnerability that exists because of two conditions:
- There is a received parameter without validation or sanitization.
- This received parameter is used to do something inside the program.
The following string receives the parameter Country and puts it in CountryStr variable:
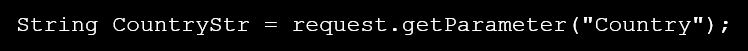
Next, if CountryStr is used in the Java Script code, an attacker could use it to send the victim a link containing malicious code. For example, to get the cookies session, send mail, show a message, etc.
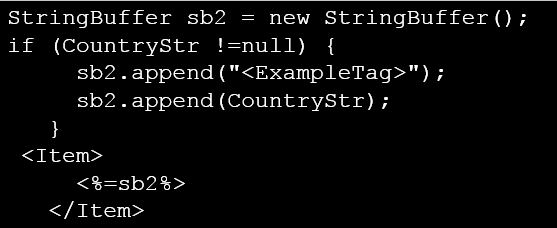
The attacker could send the following link to a victim and if the user click in that link, then the user will see their cookies:
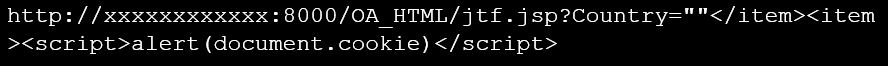
In a real life situation (not a POC), an attacker could change the link to send these cookies by email and then login with that session as the victim user. To mitigate this kind of attack, organizations should implement the provided Oracle fixes, or implement controls to detect when a user is using a url with XSS patterns. You can see OWASP XSS (Cross Site Scripting) Prevention Cheat Sheet for more information.
As you can see, this large quantity of fixed vulnerabilities shows how important it is to keep your products up to date. The threat landscape in Oracle solutions continues to expand, and this is the second time this year that a CPU has surpassed record size. Stay tuned for our next Oracle CPU blog: October 18th.
