Onapsis Research Labs First to Help Discover and Fix Vulnerabilities in SAP HANA SPS12 – SAP Security Notes December 2016
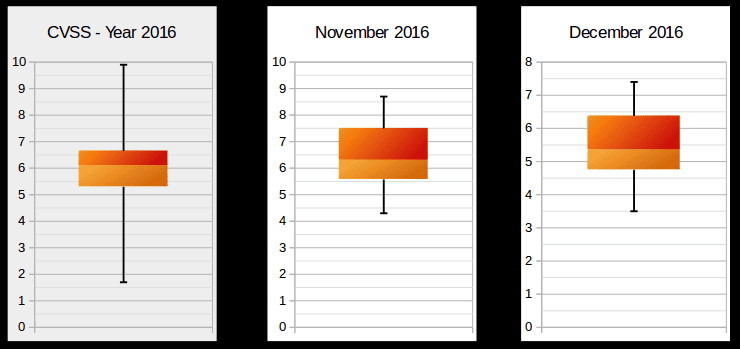
Today SAP published 23 Security Notes, making a total of 32 notes since last second Tuesday of November, considering several notes that were published outside of the normal publishing schedule. As with every month, the Onapsis Research Labs have an impact on how SAP Security evolves. This month, 6 SAP Security Notes were reported to SAP by our researchers Sergio Abraham, Nahuel Sanchez and Emiliano Fausto (all of them recognized in SAP Webpage). These notes correct 20 vulnerabilities in several platforms that our team has been researching extensively: SAP HANA and SAP For Defense. The following graph shows that this month’s release notes are more demanding compared to last month, as well as the year on average. This is because this month there are more release notes, and they are more critical in nature compared to previous months, despite there not being any hot news items: 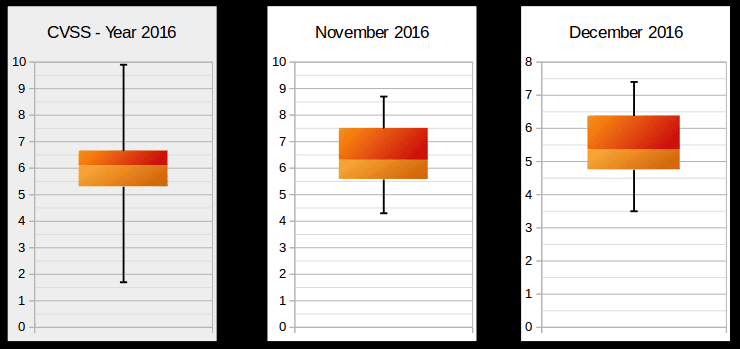
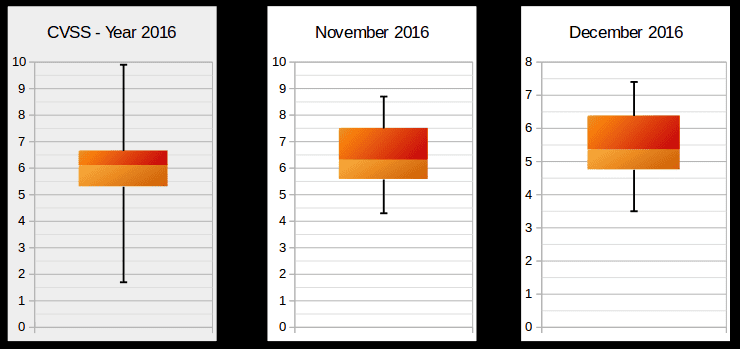
Onapsis Reported Notes: between SAP HANA and SAP For Defense
As previously mentioned, this month there are several SAP Security Notes that patch bugs reported by our Research Labs team. In fact, 20 vulnerabilities were grouped into 6 notes that can be split up based on the affected platform. Several Missing Authority Checks were grouped into three notes based on the platform. If the note is not properly installed, the products don’t perform the necessary authorization checks for an authenticated user, and this can lead on a privileges escalation. SAP Mobile Defense & Security and Defense forces and Public Security are the affected solutions in which Onapsis Researches found several function modules that were not performing the necessary authority check. After installation, authority checks will be added to ensure proper authorization to these objects. Each of these notes are categorized as medium priority, however every note has a different CVSS score. This score is based on the type of function that is affected, and what an attacker can do if the vulnerability is exploited:
- Missing Authorization check in SAP Mobile Defense & Security 1.6 (2374749). CVSS v3 Base Score: 6.3 / 10.
- Missing Authorization check in EA-DFPS monitoring tools (2376998). CVSS v3 Base Score: 4.3 / 10.
- Missing Authorization check in EA-DFPS synchronization mechanisms (2377067). CVSS v3 Base Score: 6.4 / 10.
There are also other three notes that affect SAP HANA, a platform that we have been researching since it was launched. SAP HANA is one of the newest SAP products and several customers around the world are migrating to this solution. Below is a listing of security notes affecting SAP HANA:
- Information disclosure in SAP HANA XS classic user self service (2394445). CVSS v3 Base Score: 5.3 / 10.
- Information disclosure in SAP HANA cockpit for offline administration (2351486). CVSS v3 Base Score: 4.9 / 10.
- Cross-Site Scripting (XSS) vulnerability in backup function of SAP HANA cockpit (2379342). CVSS v3 Base Score: 3.5 / 10.
The first bug is related to user information disclosure, and it is based on the message that the product shows in a specific query: valid and invalid usernames input should always show the same result to avoid that valid usernames on the system can be guessed. If the message is not the same for valid users, an attacker can brute force this resource to check whether specific usernames exists (or not) on the system. In the second case, specific functions in the SAP HANA cockpit were limited to avoid unauthorized access to OS files. Without the installation of the note, operating system files can be reached through the service, using a specific HTTP request. Despite the need to have a valid adm user in SAP HANA, that limits the chance of exploitation, even these users shouldn’t have the rights to access any file on the server. The improvements are included in SAP HANA revision 112.06 (for SPS11) and revision 122.02 (for SPS12). Update to these revisions or later revisions. It is worth mentioning that these were the first security notes released for SAP HANA SPS12 affecting directly to the database or the XS Engine. Since the launch of SAP HANA, Onapsis Research Labs have been actively helping SAP improve SAP HANA’s security, by researching and reporting dozens of bugs. To date, more than 50% of SAP HANA Security Notes came from the Onapsis Research Labs. As shown, SAP Security is not only a Netweaver issue: there are several products and solutions that need attention in order to keep them updated with the latest SAP Notes released by SAP.
High Priority SAP Notes
As mentioned, despite not having any hot news items this month, there are several security notes tagged as high priority. Here is a list of the most important SAP Security Notes of December:
- Deserialization of untrusted data in BI Platform (2265964): With the highest CVSS score of the month, this vulnerability can lead to remote command execution or even denial of service, based on well-known deserialization issue, in this case in SAP BI Platform. CVSS v3 Base Score: 7.1 / 10
- Information Disclosure in Business Objects Explorer (2336393): This note corrects the fact that some documents are created whenever an instance is deleted while running. These documents could hold confidential information without proper protection to ensure authorization. After the note is installed, no document is created in this scenario. CVSS v3 Base Score: 7.1 / 10
- Potential modif./disclosure of persisted data in BC-ESI-UDDI (2101079): This note is a re-release updating support packages and patches data, for a vulnerability that can lead to access or modification of specific information through crafted inputs on the system. CVSS Base Score: 6.8 / 10
- Missing authorization check in FM DD_DB_IMIG_CALL_INSTTOOL (1718613): This note is a typical missing authority check and it is not explicitly explained why it is a high priority correction. It is not the most relevant Security Note to take care from this list. CVSS Base Score: 4.6 / 10
The first two SAP Security Notes are critical to prioritize into your patching process and should be implemented as soon as possible. The Onapsis Research Labs are currently in the process of updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow you to check whether your systems are up to date with these latest SAP Security Notes, and ensures that those systems are configured with the appropriate level of security to meet your audit and compliance requirements. This year the Onapsis Research Labs reported bugs in more than 20 SAP Security Notes. We are working on a summary of our year in review coming to you this January, along with the fist Patch Day of 2017, stay tuned!
