Clickjacking SAP Security Notes: Where to start?

Introduction
A few months ago, we published a post about Clickjacking attacks, analyzing the nature of the attack, its related security notes and statistics on the attacks themselves. Even though this type of attack is not new, it’s an important aspect for the SAP world to understand, especially considering its relevancy after July’s security notes release. If you are an SAP user, and tried to apply some of those notes, you may have noticed that many of them are related to other Clickjacking notes, and those ones with others and so on. This could result in a complicated patching process. As a continuation of the last Clickjacking blogpost, this post provides an outline of where to begin with the application of various Clickjacking notes. In addition, this post will detail the correct process to follow in order to avoid issues in your SAP systems.
Short review: clickjacking
Let’s start by reviewing a simple question: What is Clickjacking? It is a technique used by attackers to trick users into clicking on elements that appear to be something that they are not – using the victim’s session for a malicious transaction. To be clear: Suppose a window popped-up asking you to click anywhere on it. The content would appear to advertise something harmless, but what you can’t see is that in front of the pop-up is a transparent iframe tag holding a reference to a malicious portal (whatever you can imagine). This iframe could be short, transparent and laid-out to only expose the area that the attacker wants you to click over. In addition, this area can move in accordance with your mouse to ensure that it will capture any click you make. There are many examples of Clickjacking attacks it is possible to be exposed to, and while it is true that you could avoid it by being careful where you click, it is still not safe enough. It is recommended to have a second line of defense in order to protect against these types of attacks. This additional layer of defense is what SAP has provided in their Clickjacking security notes, whitelisting only the hosts allowed to reference critical services through this method. The best starting point for understanding how to apply Clickjacking security notes for SAP is to read note 2319727. Here you will find a full overview of the notes you need to follow in order to protect both your ABAP and JAVA services. In general, there are two groups of notes, one for JAVA and another one for ABAP platforms, each of which has a main note to provide whitelist framework support. Additionally, you have a sub-group of associated notes detailing how to secure other specific services. More details are provided below.
ABAP Clickjacking Notes
SAP provides four frameworks to protect different ABAP services, all of them are based in the whitelist implemented by note 2142551 “Whitelist service for Clickjacking Framing Protection in AS ABAP”. These frameworks are described in the following notes:
- Business Server Page (BSP), described in note 2319192.
- SAP GUI for HTML, described in note 2319172.
- NetWeaver Business Client (NWBC) for HTML, described in note 2319174.
- WebDynpro ABAP, described in note 1872800
- .
As you can see in the below picture, there are additional notes that should be applied for the different frameworks in order to complete a full implementation of clickjacking security notes. For example, if you want to apply note 2319192 (BSP Clickjacking protection), you will have to apply notes 2215694 and 2119535 beforehand. We recommend following the instructions detailed in each framework note in order to apply each note in the correct order and with the correct method.
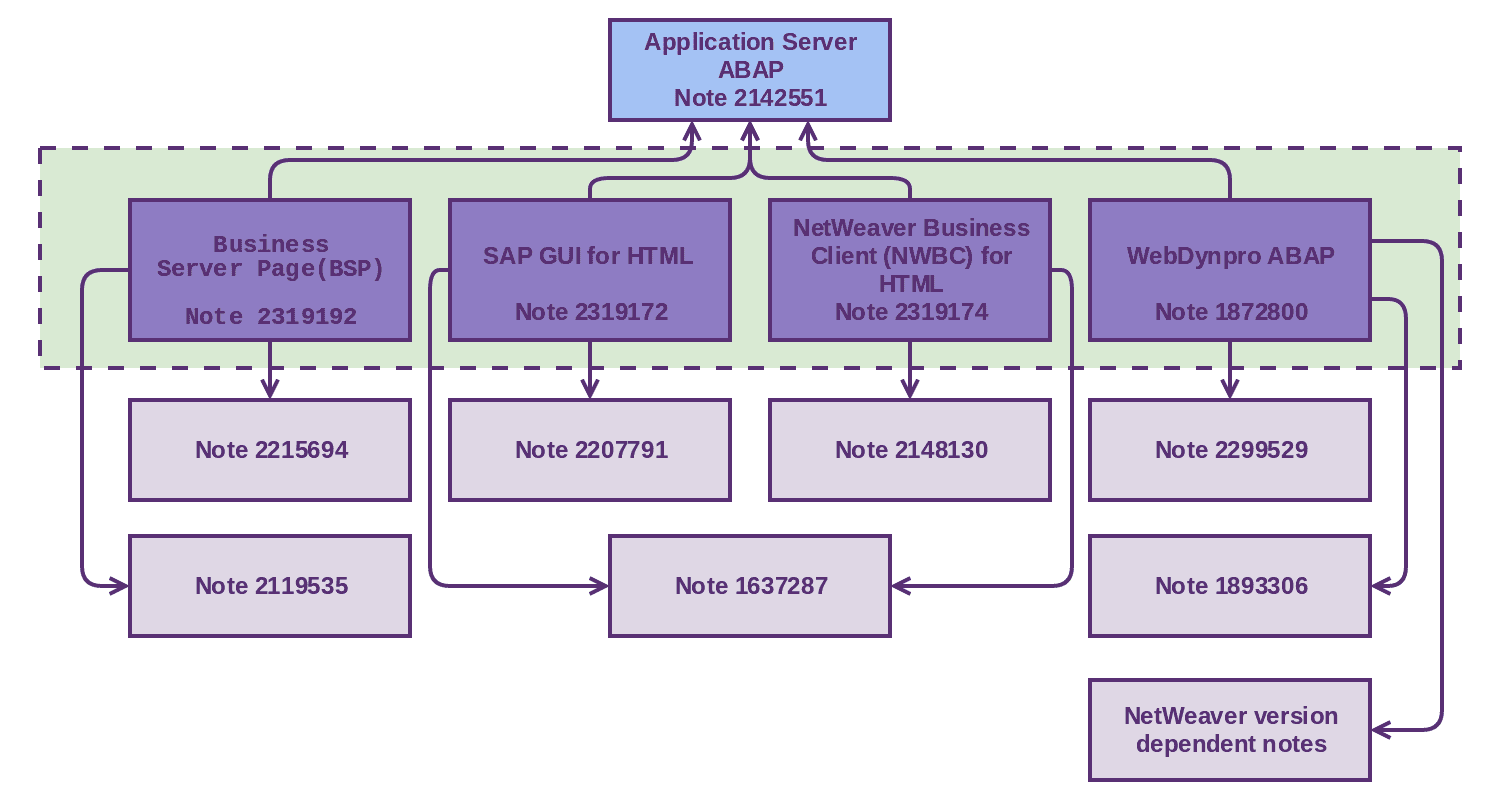
Within the dotted rectangle, you can see the framework notes highlighted in blue. Related to those are additional notes that are required to complete the installation. As you can see, all framework notes depend on note 2142551, therefore it is critical to make sure that this note is correctly implemented before implementing any of the others.
JAVA Clickjacking Notes
As with ABAP, SAP provides frameworks for the different services based on JAVA. The main note that must be applied as a prerequisite is note 2170590 “Whitelist service for ClickJacking Framing Protection in AS JAVA” which implements the base requirements needed on the JAVA framework. Because JAVA notes are more intertwined than notes for ABAP, we’ve provided greater details below:
- Web Dynpro JAVA (WDJ), described in note 2169860.
- This note in particular supports two kinds of fixes, one using clickjacking whitelist and the other using headers modification (“X-FRAME-OPTIONS” header with value “SAMEORIGIN”). SAP recommends using a whitelist solution whenever possible.
- Another WebDynpro related note is 2286679, which gives support to WDP developers.
- Web Channel Experience Management (WCEM), described in note 2244161.
- As JAVA Web Dynpro, WCEM refers to note 1781171 (header modification) and note 2042829, but for this scenario, a whitelist solution is not supported.
- Java Server Pages (JSP), described in note 2290783.
- It refers to note 2286679 (JAVA ClickJacking API implementation and description).
- Enterprise Portal, described in note 2169722.
- This note provides remediation necessary for protecting the Enterprise Portal (referring to note 2276701).
The following picture details a complete overview of the relationships among these notes:
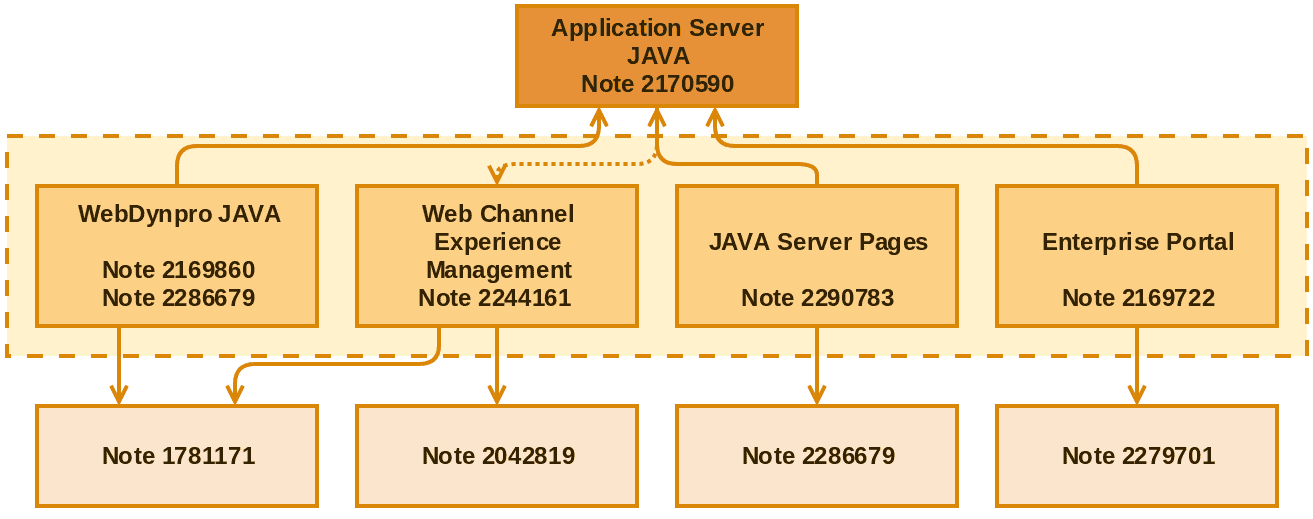
The dotted arrow from Application Server Java to Web Channel Experience Management represents relation, not dependency. As in the ABAP notes description, the dotted rectangle includes the framework notes. All framework notes depend on note 2170590, therefore it is critical to make sure that this note is correctly implemented before implementing any of the others.
Conclusion
Even though Clickjacking is not a critical attack and implementation of these notes is not a particularly simple task, implementing this solution helps to reduce the attack surface. We strongly recommend applying and installing all security notes depending on your implementation. Onapsis Research Labs have updated the Onapsis Security Platform to reflect these security notes to ensure that customers receive continued protection against clickjacking attacks. We strongly believe this post will help your team to analyze and implement the correct solution for complex Clickjacking security notes. For additional information or assistance, please do not hesitate to contact us directly at [email protected].



