Analyzing SAP Security Notes March 2016
SAP is a complex and ever changing system, whether because of changes introduced to your SAP implementation to better suit your business or through the application of Security Notes (Patches) to ensure that newly disclosed vulnerabilities are mitigated.
In order to provide a predictable and scheduled flow of vulnerability mitigation information and security patches, SAP releases the major part of their latest Security Notes information on the second Tuesday of every month. Due to this regular disclosure of new security issues that could potentially weaken the security of SAP systems within an organization, it’s highly recommended to carry out periodic assessments on a monthly basis at least.
At Onapsis we are very concerned about our client’s SAP system security and also the state of SAP security in general, so to assist our customers, we perform a detailed analysis of the monthly SAP Security Notes as soon as they are published. The goal of this is to provide SAP clients with detailed information about the newly released notes and vulnerabilities affecting their SAP systems and help guide their testing of these systems within their organization.
Between the last published SAP Security Tuesday and today, there were 28 SAP Security notes published by SAP AG (taking into account 10 Support Packages and 18 Patch Day Notes). The Onapsis Research Labs contributed as almost every month, on reporting vulnerabilities found in the SAP Software (Acknowledgments to Security Researchers).
The SAP Security Note released this month, related to a Hot News priority advisoriy reported by the Onapsis Research Labs was:
- 2260344; 9.0 (AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:H/A:H). OS command injection vulnerability in SCTC_* Function modules
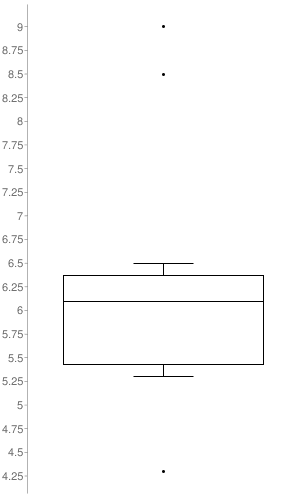
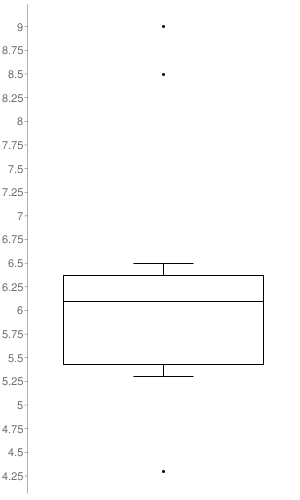
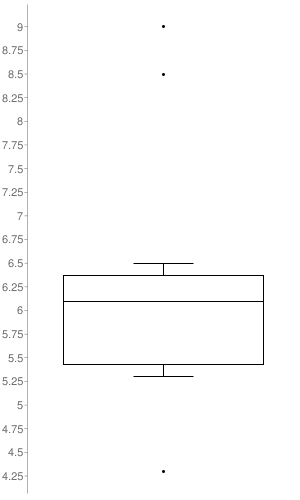
The box-plot graph illustrates the distribution of CVSS v3 scores across the Security Notes released. The only notes taken into account to build it, were the ones to which SAP set a CVSS v3 (16 out of the 28 SAP Security Notes). As it’s represented in the graph, the SAP Security Notes range values go from 4.3 to 9.0 with a median of 6.1.
Hot News from SAP
- 2260344 – 9.0 (AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:H/A:H). OS command injection vulnerability in SCTC_* Function modules. This Note fixes certain function modules callable through the transaction SE37, which could let an attacker execute arbitrary OS commands in the SAP System.
- 2281195 – No CVSS v3 provided. Potential remote termination of running processes in SAP Visual Enterprise Author, Generator and Viewer. This Note fixes a vulnerability present in the applications:
- SAP Visual Enterprise Author 8.0 SP04 MP3
- SAP Visual Enterprise Generator 8.0 SP04 MP3
- SAP Visual Enterprise Viewer 8.0 SP04 MP3
Through the exploitation of a vulnerable plugin present in these applications, an attacker may cause a Memory Corruption which would lead to the termination of the app, rendering it unusable until manually restarted.
SAP Security Notes with higher CVSS scoring provided by SAP
- 2037304 – *8.5 (AV:N/AC:M/Au:S/C:C/I:C/A:C). Lack of proper input validation in SDCC Download Function Module. The note addresses a Service Data Control Center function module, which was not validating input parameters.
- 2223688 – 6.5 (AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H). Potential denial of service in Message Server. The note fixes a vulnerability in the message server. An attacker may send an specific request to make the message server exhaust its resources, thus rendering the system unavailable.
- 2235994 – 6.4 (AV:A/AC:H/PR:H/UI:N/S:U/C:H/I:H/A:H). Untrusted XML input parsing possible in Configuration Wizard. The note fixes an XML eXternal Entity type vulnerability, through which a malicious user may send a specially crafted XML content to perform a Denial of Service or retrieve data from the affected SAP System.
- 2210310 – 6.3 (AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L). Unauthorized use of application functions in NavigationServlet. The note addresses a vulnerability, which could allow an attacker to execute functions in Navigation Servlet without proper authentication nor authorizations.
- 2269315 – 6.3 (AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L). Missing authorization check in OAuth2 Server Runtime. The note covers a security problem in the OAuth2 Server Runtime. In certain ICF configurations, an already authenticated user may use the OAuth2 access token to access OData services to which access should be restricted.
- 2253850 – 6.3 (AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L). XML External Entity vulnerability in RTMF. The note addresses an XXE (eXternal XML Entity) type vulnerability in the Real Time Messaging Framework, through which a malicious user may send an specially crafted XML file to cause a Denial of Service or retrieving of information from the affected system .
*Note: This was the only CVSS value provided as version 2, the rest of them were calculated version 3 of CVSS
Other attack vectors
- Reflected Cross-site Scripting (XSS): Notes 2204581, 2238765, 2238375, 2189174, 1676754
- Stored Cross-site Scripting (XSS): Note 2219896
- Missing authorization check: Notes 2069820, 2064501, 1658568
- Directory Traversal: Note 2234971
- XML External Entity (XXE): Note 2085214
- Information Disclosure: Notes 2258786, 2260895, 1771200, 2255990, 2196420, 2069994
- Update to an SAP Security Note: The Note 2071329 updates the SAP Security Note 1676754
- Hard coded User Credentials: Note 1905286
- Weak sensitive data encryption: Note 2282338
Each month Onapsis updates its flagship product Onapsis Security Platform (OSP) to allow you to check whether your systems are up to date with these latest SAP Security Notes as well as ensuring those systems are configured with the appropriate level of security to meet your audit and compliance requirements.
Stay tuned for next month’s Security Notes analysis from the Onapsis Research Labs.
NOTE:
SAP published their monthly post in their SCN space “The Official SAP Product Security Response Space”, providing information about the SAP Security Notes.
Here it’s the link to the SAP blogpost: “SAP Security Patch Day – March 2016”
As they announce in their official site, from now on, the CVSS version 3 will be used in the SAP Security Notes prioritization.

