Analyzing SAP Security Notes January 2016
SAP is a complex and ever changing system, whether because of changes introduced to your SAP implementation to better suit your business or through the application of Security Notes (Patches) to ensure that newly disclosed vulnerabilities are mitigated.
In order to provide a predictable and scheduled flow of vulnerability mitigation information and security patches, SAP releases the major part of their latest Security Notes information on the second Tuesday of every month. Due to this regular disclosure of new security issues that could potentially weaken the security of SAP systems within an organization, it’s highly recommended to carry out periodic assessments on a monthly basis at least.
At Onapsis we are very concerned about our client’s SAP system security and also the state of SAP security in general, so to assist our customers, we perform a detailed analysis of the monthly SAP Security Notes as soon as they are published. The goal of this is to provide SAP clients with detailed information about the newly released notes and vulnerabilities affecting their SAP systems and help guide their testing of these systems within their organization.
Between the last published SAP Security Tuesday and today, there were 23 SAP Security notes published by SAP AG (taking into account 3 Support Packages and 20 Patch Day Notes). The Onapsis Research Labs contributed as almost every month, on reporting vulnerabilities found in the SAP Software (Acknowledgments to Security Researchers).
The SAP Security Notes released this month, related to advisories reported by the Onapsis Research Labs were:
- 2246277; 6.4 (AV:N/AC:L/Au:N/C:P/I:P/A:N). SAP ORACLE insecure authentication scheme
- 2233550; 5.8 (AV:A/AC:H/Au:N/C:C/I:P/A:P). Communication encryption for HANA multi tenant database containers does not work as expected
- 2233136; 4.9 (AV:N/AC:H/Au:S/C:N/I:N/A:C). Potential termination of running processes triggered by IMPORT statement
- 2252941; 1.7 (AV:L/AC:L/Au:S/C:P/I:N/A:N). Potential information disclosure relating to files exported from SAP HANA with EXPORT statement
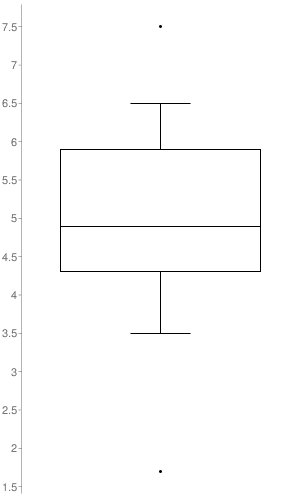
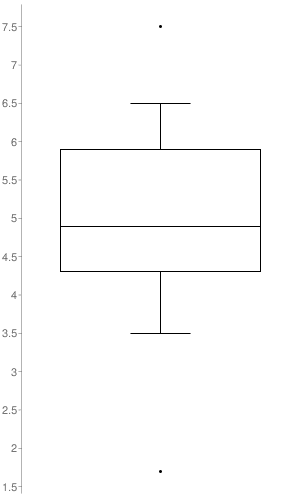
The plot graph illustrates the distribution of CVSS v2 scores across the Security Notes released. The only notes taken into account to build it, were the ones to which SAP set a CVSS v2 (17 out of the 23 SAP Security Notes). As it’s represented in the graph, the SAP Security Notes range values go from 1.7 to 7.5 with a median of 4.9.
Hot News from SAP
There were no Hot News published this month.
SAP Security Notes with higher CVSS scoring provided by SAP
- 2247644 – 7.5 (AV:N/AC:L/Au:N/C:P/I:P/A:P). PI SEC: Security vulnerabilities found in Apache Groovy Library used in PI Cloud Integration Content. This vulnerability is linked to CVE-2015-3253, which has been addressed last month in SAP Security Note 2248673. The problem resides in a library called Apache Groovy, which is used by the component Integration Gateway.
- 2221986 – 6.5 (AV:N/AC:L/Au:S/C:P/I:P/A:P). Too many privileges assigned to HANA hdbrole. The note improved the privileges of a role provided by SAP HANA Rules Framework, such privileges permitted the user to access objects in a particular schema to which access should be forbidden.
- 2246277 – 6.4 (AV:N/AC:L/Au:N/C:P/I:P/A:N). SAP ORACLE insecure authentication scheme. The note fixes the value of a parameter (which has been already deprecated), which value turns to be insecure when SAP secure store is used for an Oracle 11.2 database connection.
- 2248735 – 6.0 (AV:N/AC:M/Au:S/C:P/I:P/A:P). Code injection vulnerability in System Administration Assistant. The note fixes a high priority vulnerability, through which an authenticated atacker could be able to abuse the SAP System Administration Assistant and execute arbitrary Operating System commands.
- 2233550 – 5.8 (AV:A/AC:H/Au:N/C:C/I:P/A:P). Communication encryption for HANA multi tenant database containers does not work as expected. The note fixes a security bug which affected only the SAP HANA multi tenant database container installations. The problem resided in the mechanism used by the application to authenticate and encrypt communications between the tenant’s internal services. By abusing this vulnerability, a potential attacker would be able to eavesdrop the communication or to connect to a tenant (to which access is not allowed) through other tenant in the same SAP HANA host.
- 2193424 – 5.0 (AV:N/AC:L/Au:N/C:P/I:N/A:N). Potential information disclosure relating to NavigationServlet. The note fixes an information disclosure vulnerability, which could be abused by a non authenticated user to discover data from the user using NavigationServlet.
- 2241978 – 5.0 (AV:N/AC:L/Au:N/C:N/I:P/A:N). Log injection and missing size restriction in SAP HANA Extended Application Services Classic (XS). The note fixes a security bug in SAP HANA Extended Application Services Classic (XS), through which a non authenticated attacker may issue specially crafted HTTP requests to forge additional logging in the trace files of the XS process and consume disk space of the HANA system. The space consumption has a fixed limit, and a log rotation mechanism implemented by default in the product; anyway, specially crafted HTTP requests can consume the available memory buffers in the XS process making it crash.
Other corrections with High Priority (no CVSS provided by SAP)
- 2262645 – Security vulnerability in Apache Commons Collections library used by multiple SAP Sybase products.
- 2249347 – Security vulnerabilities found in Apache Commons Collections library used in ep.runtime.common.
Both SAP Security Notes are linked, as certain versions of SAP Enterprise Protal and SAP Sybase products were using an open source framework called Apache Commons Collections library; which had been detected to have security issues (Denial of Service and Remote Code Execution during object de-serialization), the notes bring a new version of this framework which is updated and not vulnerable. - 1973081 – XSRF vulnerability: External start of transactions with OKCode. The note provides switchable white lists as a generic solution for Cross-Site Request Forgery, the idea of this feature is to run in the SAP back-end and to give cross application protection for SAP Administrators against Cross-Site Request Forgery attacks.
- 2243373 – Potential denial of service in BC-WD-JAV. The note provides a fix to solve a “Denial of Service” vulnerability which could be issued through the exploitation of an excessive resource consumption of the Webdynpro java application. The attacker would trigger this condition by generating a specially crafted request to the java application, thus causing a denial of service.
Other attack vectors
- Reflected Cross-site Scripting (XSS): Notes 2206793, 2239015, 2234918, 2227310, 2224249
- Missing authorization check: Notes 2251619, 2248862, 1949253
- Information disclosure: Notes 2167813, 2191290, 2252941
- Denial of Service: Note 2233136
Each month Onapsis updates its flagship product Onapsis Security Platform (OSP) to allow you to check whether your systems are up to date with these latest SAP Security Notes as well as ensuring those systems are configured with the appropriate level of security to meet your audit and compliance requirements.
Stay tuned for next month’s Security Notes analysis from the Onapsis Research Labs.
NOTE:
SAP published their monthly post in their SCN space “The Official SAP Product Security Response Space”, providing information about the SAP Security Notes.
Here it’s the link to the SAP blogpost: “SAP Security Patch Day – January 2016”

