SAP Security Patch Day August 2021: Critical Patches Released for Various Applications

Highlights of August SAP Security Notes analysis include:
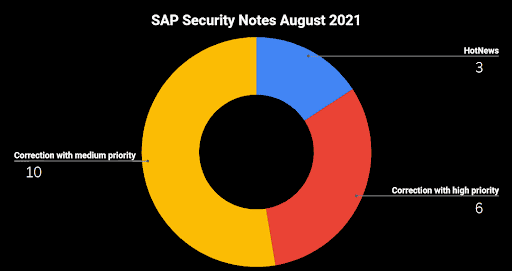
- August Summary—19 new and updated SAP security patches released, including three HotNews Notes and six High Priority Notes
- Two patches released with CVSS score 9.9—SAP Business One and SAP NetWeaver Development Infrastructure affected
- Onapsis Research Labs Collaboration—Onapsis Researcher Yvan Genuer found multiple vulnerabilities in SAP Enterprise Portal, three rated with High Priority
SAP has published 19 new and updated Security Notes on its August Patch Day. This includes three HotNews Notes and six High Priority Notes.
It seems that last month’s patch day was the “calm before the storm”. With nine critical patches in total (considering patches with HotNews and High Priority as critical), SAP customers are facing the most noteworthy SAP Patch Day this year. The small group of SAP applications that are affected by a CVSS 9.9 vulnerability in 2021 is now extended with SAP Business One and SAP NetWeaver Development Infrastructure. SAP Enterprise Portal customers should pay special attention to SAP’s August Patch Day since there are four patches released for this application, in collaboration with the Onapsis Research Labs, three of them rated as High Priority.
The HotNews Notes in Detail
SAP Security Note #3071984, tagged with a CVSS score of 9.9, patches a vulnerability in SAP Business One that allows an attacker to upload files, including script files, to the server. The only reason it does not have a CVSS 10 rating is because it needs a minimum set of authorizations. Fortunately, there is a workaround available for customers who can not immediately apply the related hotfix—they can simply deactivate the affected functionality. But, as always, SAP emphasizes that this workaround should be considered a temporary fix rather than a permanent solution.
Another CVSS 9.9 vulnerability was patched with SAP Security Note #3072955. A servlet of the Component Build Service in SAP NetWeaver Development Infrastructure (SAP NWDI) was exposed to the outside, allowing attackers to perform proxy attacks by sending crafted queries. According to SAP, the impact of this vulnerability depends on whether or not SAP NetWeaver Development Infrastructure (NWDI) runs on the intranet or Internet. If it is running on the Internet, this vulnerability “could completely compromise sensitive data residing on the server, and impact its availability”.
The third HotNews Note is SAP Security Note #3078312, tagged with a CVSS score of 9.1. It patches an SQL Injection vulnerability in the Near Zero Downtime (NZDT) tool of the DMIS Mobile Plug-In or SAP S/4HANA. The tool is used by SAP’s corresponding nZDT service for time-optimized system upgrades and system conversions. When using the nZDT service, the maintenance is performed on a clone of the production system. All changes are recorded and transferred to the clone after the maintenance tasks are completed. During the final downtime, only a few activities are executed, including a switch of the production to the new system (clone).
In addition to the correction instructions that come with the note, there is also a workaround available for all customers who have activated the Unified Connectivity (UCON) runtime check. The workaround for the vulnerability within the tool used by the nZDT service is to not assign the used remote-enabled function module to any communication assembly (CA) in UCON.
Critical SAP Enterprise Portal Patches Released in Collaboration with The Onapsis Research Labs
A special recognition goes to my colleague Yvan Genuer from the Onapsis Research Labs who supported SAP in fixing four vulnerabilities in SAP Enterprise Portal:
High Priority SAP Security Note #3073681, tagged with a CVSS score of 8.3, patches a Cross-Site Scripting (XSS) vulnerability caused by one of the portal’s servlets. An insufficient sanitization allows the injection of Javascript into the corresponding web page. If a victim navigates to an infected servlet, the vulnerable script is executed in their browser. Although the impact on the system’s confidentiality, integrity and availability is high, the fact that it is highly complex and requires user interaction for the exploit to succeed, mertis a lower CVSS score. SAP Security Note #3072920, also tagged with a CVSS score of 8.3, patches a very similar vulnerability in another servlet of the SAP Enterprise Portal. So it’s no surprise that it has also the same CVSS value and vector assigned as note #3073681.
The third High Priority Note is SAP Security Note #3074844, tagged with a CVSS score of 8.1. It patches a Server Side Request Forgery (SSRF) vulnerability in one of the design time components of the SAP Enterprise Portal. It allows an unauthenticated attacker to craft a malicious url which, when clicked by a user, can make any type of request (e.g. POST, GET) to any internal or external server.
The fourth vulnerability that was patched by SAP in collaboration with the Onapsis Research Labs is described in SAP Security Note #3076399, tagged with a CVSS score of 6.1. The note patches a URL Redirection vulnerability in SAP Knowledge Management. It allows remote attackers to redirect users to arbitrary websites and conduct phishing attacks via a URL stored in a component. This gives the attacker the ability to compromise the user’s confidentiality and integrity.
Further critical SAP Security Notes in August
SAP Security Note #3057378, tagged with a CVSS score of 8.8, patches a programming error that affects authentication in all SAP systems that are accessed through a SAP Web Dispatcher, if authentication based on X.509 client certificates is used. The error prevents SAP Web Dispatcher from processing any authentication checks for functionalities that require user identity. As a result, an attacker with network access can execute functions in SAP application systems with any user identity that has a mapping to an X.509 certificate.
SAP Security Note #3067219, tagged with a CVSS score of 7.6, patches a Task Hijacking vulnerability in SAP Fiori Client Native Mobile for Android. According toSAP, this vulnerability allows attackers to take over legitimate apps and steal users’ sensitive information. There is a temporary workaround for SAP customers using a customized Fiori client. However, this workaround depends on the method used to build the customized Fiori client.
SAP Security Note #3073325, tagged with a CVSS score of 7, patches a Missing Authentication vulnerability in SAP Business One. It can enable an attacker who has access to the victim’s browser to login as the victim without knowing their password. The attacker could obtain highly sensitive information and use it to take substantial control of the vulnerable application. There is an optional workaround but it does not seem to be sufficient.. Since the referenced SAP Business One hotfix is needed anyway in order to fix HotNews Note #3071984 (and a third SAP Business One vulnerability, described in SAP Security Note #3078072), it is strongly recommended that the hotfix should be applied instead of the optional workaround.
Summary and Conclusions
With nineteen new and updated Security Notes, including three HotNews Notes and six High Priority Notes, this is a robust SAP Patch Day.
The possible workaround for HotNews Note #3078312 clearly demonstrates that security mechanisms like the Unified Connectivity (UCON) runtime check should be activated whenever possible. These not only deliver an additional degree of security for customers systems—they can also enable quick patching for detected vulnerabilities
A special recognition goes also to the security team at SAP. They quickly provided patches for the three High Priority portal issues. The Onapsis Research Labs reported these vulnerabilities at the end of June 2021 and the SAP team provided patches for these issues overnext Patch Day. This is really impressive given the large number of different releases and environments to be tested. It is certainly also the result of two facts:
- The meticulous pre-analysis of new detected vulnerabilities through the Onapsis Research Labs before they are reported to SAP
- The well established communication channel between Onapsis and SAP that allows quick answers to questions that sometimes come up during patch creation
As always, Onapsis Research Labs continuously updating The Onapsis Platform to incorporate newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
Further Reading
- This joint report from Onapsis and SAP analyzes how threat actors are actively targeting unprotected SAP applications.
- Onapis and SAP address how to protect your organization’s business-critical applications from the looming threat of ransomware.
