SAP Security Notes February 2020: Calm Times Are Over—19 New SAP Security Notes and Root Access at Risk
Highlights of February SAP Security Notes analysis include:
- Onapsis significantly contributes to SAP’s February Patches—12 reported vulnerabilities fixed by SAP with 5 Security Notes—2 High Priority Notes and 3 Medium Priority Notes
- High Priority issues solved in SAP Host Agent and SAP Mobile Platform SDK—Fixes solve a DOS and a Missing Authorization vulnerability
- Special attention required on upcoming Chromium Updates—Major impact on SAP applications expected
Everyone who hoped that SAP Patch Days would remain calm as we saw in January has now gotten a quick dose of reality with a busy February. With a total of 17 new and updated SAP Security Notes today and two updated Notes at the end of January, the number of new Notes is on the increase. Even though there is only one HotNews Note this month, the well-known update on the supported Chromium version in SAP Business Client, there are another four High Priority Notes to take into account due to their criticality. The Onapsis Research Labs has contributed to two of the High Priority Notes and three of the Medium Priority Notes, which fix a total of 12 vulnerabilities and represent more than 30% of the new SAP Security Notes published this month, not considering re-released ones. This significant contribution demonstrates Onapsis’s commitment to keeping SAP customers protected.
February Patch Day Marked by Onapsis—9 Root and <SID>adm Privilege Escalation Issues Detected in SAP Landscape Management
With five SAP Security Notes fixing 12 vulnerabilities in total, more than 30% of the February Security Notes were initiated by the Onapsis Research Labs, not considering re-released ones.
SAP Security Notes #2877968 and #2878030, both rated as High Priority with a CVSS of 7.2, fix Root and <SID>adm Privilege Escalation vulnerabilities in SAP Landscape Management. SAP Landscape Management is used to administer large SAP landscapes very efficiently through automation of repetitive, and often time-consuming, administrative tasks. It also provides advanced operations for SAP HANA and SAP S/4HANA. The solution uses the SAP Host Agent that is installed on each SAP System to collect the required system information as well as to execute operations remotely across the landscape.
The Onapsis Research Labs has identified nine of these operations to be vulnerable. Due to missing sanitization, the vulnerability can allow an attacker to inject the operational commands with malicious content. Depending on the specific operation, this content is executed in the context of user Root or <SID>adm. The impact of the vulnerability on the confidentiality, integrity, and availability of the system is therefore rated with High. Both Notes solve slightly different scenarios. Note #2877968 covers all operations that can directly be infected with vulnerable commands. Note #2878030 handles operations that will first need to place an infected binary on the target host in order to exploit the vulnerability.
Onapsis also helped SAP in patching another three issues, all tagged as Medium Priority. SAP Security Notes #2836445, #2838835 and #2695210 fix Information Disclosure vulnerabilities in different components, that were also detected by the Onapsis Research Labs. All rated with CVSS scores of 5.3, they can be exploited to gather information about the technical infrastructure of the affected component. This type of information can be used later by an attacker to start the “real” attack.
SAP Security Note #2836445 describes a vulnerability in the architecture of the saposcol executable. This executable is used to monitor the hardware of an SAP system and uses the shared memory for interprocess communication. The shared memory is not protected sufficiently, so an unprivileged user can potentially access it and get information about CPU, RAM, directory sizes and other system attributes. Take into account that during our research to report this vulnerability, we discovered that if a customer has an older version of SAP Host Agent, this vulnerability allows chaining with an older weakness to achieve root privileges. So, it is important to ensure that you have SAP Host Agent 7.21 PL 26, saposcol v2.38 or above. If not, applying this Security Note should be a higher priority, despite being currently designated as a Medium Priority one.
SAP Security Note #2838835 fixes an issue with several endpoints in SAP NetWeaver AS Java. These endpoints expose information about the system, like hostname, server node and installation path. Finally, SAP Security Note #2695210 solves an issue in SAP Business Objects that allows an attacker to exploit a specific Java Server Page to scan the network for available hosts and services.
Two High Priority Notes Covering SAP Host Agent and SAP Mobile Platform SDK
SAP Security Note #2841053 with a CVSS rating of 7.5 solves a Denial of Service (DOS) vulnerability in SAP Host Agent. The vulnerability exists in scenarios based on user/password authentications and is caused by the fact that SAP Host Agent’s authentication uses facilities provided by the underlying operating system. These facilities often delay failed authentication requests in order to handle the negative impact of brute force authentication attacks. SAP Host Agent limits the number of parallel authentication requests so that regular authentication requests might be slowed down due to delayed responses. Possible solution options are:
- Restricting access ports to the datacenter network
- Restricting access ports to trusted networks and addresses only through maintenance of SAP Host Agent’s Access Control List
- Only allowing certificate-based authentication (only for SAP Host Agent version 7.21 PL45 and higher)
The other High Priority Note #2695776, titled “Missing Authorization Check in SAP Mobile Platform Native SDK, Android” with a CVSS score of 7.4 fixes an issue in which data stored in the Federation Library was not protected by default. So if the application developer did not explicitly define their own permission to access the library data, it was unprotected. SAP has now published a new Federation Library that contains a default signing permission. In order to not force all developers to include the updated Federation Library in each application and rebuild it, an explicitly assigned permission will still overwrite the newly introduced default permission.
Stricter Cookie Handling in Google Chrome Version Will Affect SAP Applications
Facing the new update on the supported Chromium version for SAP Business Client, we want to take the opportunity to point to an important issue: as of version 80 of Google Chrome, the default handling of cookies will be changed significantly. In order to provide better protection against Cross-Site Request Forgery (CSRF) attacks, Chrome will set the default value of the SameSite cookie attribute to “Lax” if no explicit value is specified by the server. This will have a negative impact on applications, which integrate multiple web sites within a single browser window as they often rely on cross-domain cookies. We strongly recommend that you read SAP HotNews Note #2887651, which describes the affected SAP components, possible solutions, and further details.
Summary & Conclusions
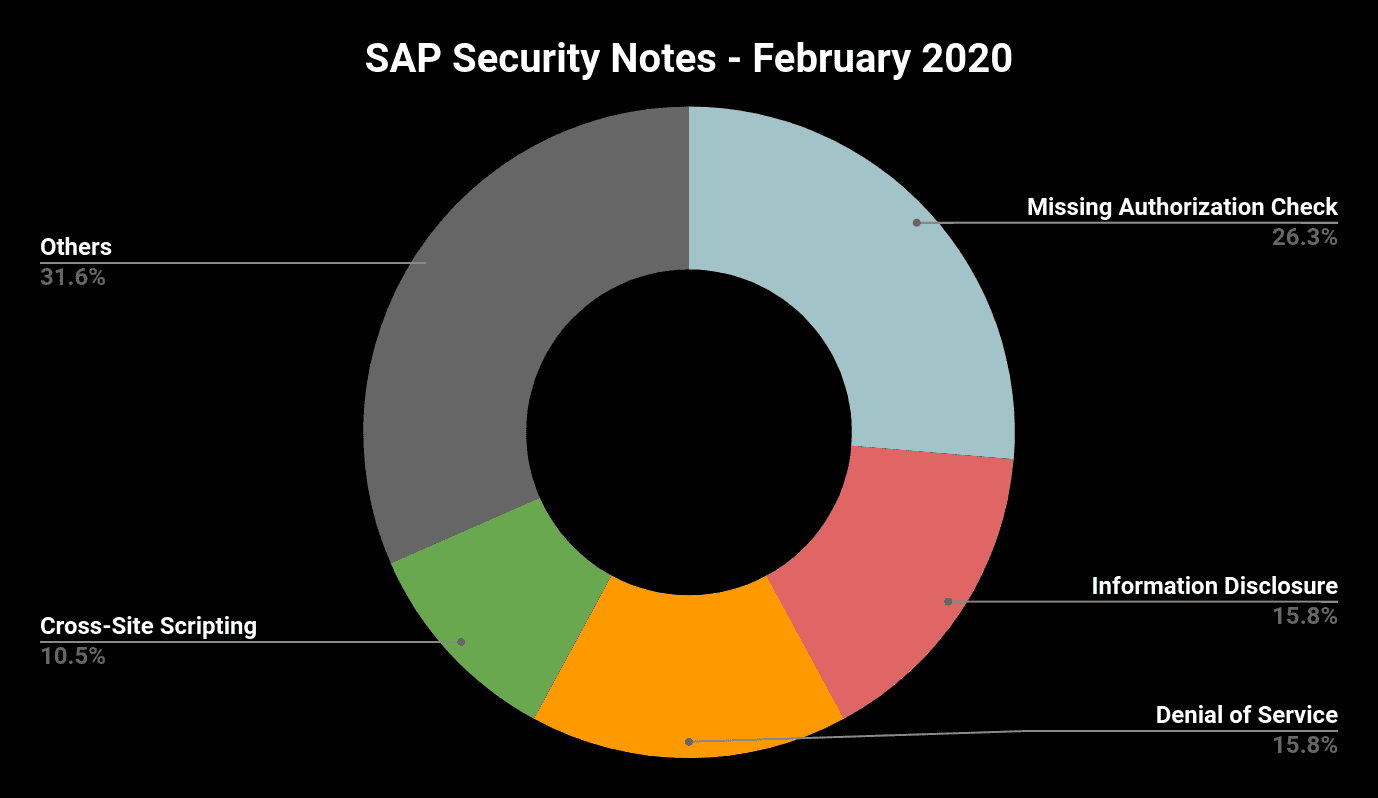
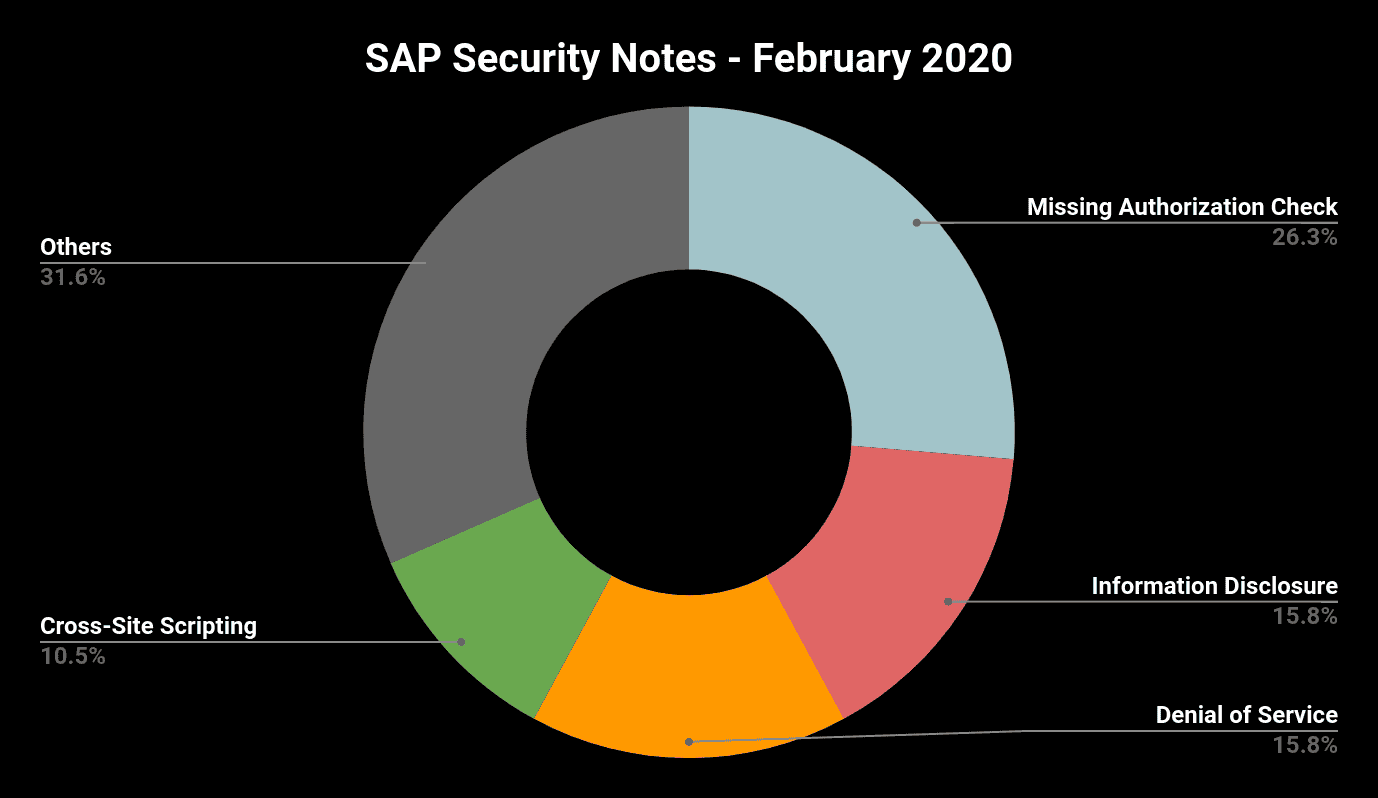
The 14 SAP notes released in January represented a very calm beginning of the year. With 19 new Notes this month, we are back to a busy month with more notes and more critical ones included. Helping keep its customers protected, the SAP Security Team continues to get significant help from the Onapsis Research Labs to ensure its products are secure through patches. Once again several members from the Onapsis team (Five!) are recognized by SAP in its Acknowledgments to Security Researchers. Here’s a summary of this month notes by type:
The Onapsis Research Labs is already working to update The Onapsis Platform to incorporate these newly published vulnerabilities into the product so that our customers can check missing notes during their security assessments. Finally, this year we are planning to share with our customers and general audience more data about our analysis of the SAP Security Notes, among other content and knowledge from our team. Based on this, we will be doing a webinar next week to go a little bit deeper into the SAP Security Notes of the month, sharing all the analysis our team did today and will keep doing during the week. Register for the SAP Security Notes February 2020 webinar here.
