SAP Security Notes August 2017: Remote Code Injection Vulnerability in JAVA Component
Editor Note: This blog post was updated on March 20, 2025
It’s the second Tuesday of the month, meaning another round of monthly SAP notes have been released. Below is our monthly analysis regarding the SAP vulnerabilities fixed, to help you keep your ERP environment safe and protected. For another month, there are no new notes tagged as Hot News, now making a four month streak in which notes of this severity are absent. There is still a need for action however, since three notes were reported as having High priority. One of these High priority notes concern a code injection vulnerability that was reported by the Onapsis Research Team.
SAP released a batch of 18 notes today, summing up to a total of 20 notes since the previous second Tuesday of the month. In the following sections we will explain this code injection vulnerability in more detail, along with some details of the other two notes marked as High. All of these vulnerabilities deserve immediate attention and should be patched sooner rather than later.
Code Injection vulnerability in Visual Composer
The Visual Composer is a web application which runs fully inside the browser. The Visual Composer allows business consultants to build Enterprise Portal content without writing a single line of code. This can be done by using logical portal building blocks which are called integrated views (iViews). An iView represents a visual application (or part thereof), and can process data from back-end systems. This specific vulnerability applies to iViews created in 04s versions.
The vulnerability, discovered by Matias Mevied of Onapsis Research Labs, allows attackers to inject malicious code into the back end application. By simply having end users access a specially crafted URL, unwanted applications can be started on the client machine by an attacker. Depending on who makes use of your Enterprise Portal, clients in this sense could be employees, customers, partners or suppliers.
The SAP Security Note released following this discovery is #2376081. It is one of three high risk bugs this month, and is tagged with a CVSS v3 base score of 7.4 / 10. This high score follows the facts that the vulnerability is not intricate to exploit and affects additional systems beyond only the vulnerable one. The additional affected systems could be the client systems of end users accessing the Enterprise Portal.
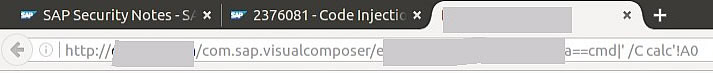
The following image shows how simple an attacker can execute code through the affected component. In this proof of concept, Windows Calculator will be opened after the user accesses this URL from an unpatched SAP system:
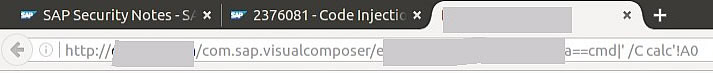
A large number of Visual Composer versions, starting from 7.00, are affected. Therefore, due to the affected version scope, even when this component might not be actively used in your organization, it has an increased probability of being part of an attack. Definitely consider patching the vulnerability before providing access to the Enterprise Portal to organizations outside of your own, since the consequences might go beyond having to write an internal email to your employees.
High Priority Notes details
There are another two high priority notes released this month which are tagged by SAP as High Priority Notes. You will find their details below, including CVSS score, which is almost the same for all three high priority notes this month. One of the two other high priority notes also affect SAP Netweaver over JAVA, just as the one reported by Onapsis. The second one affects SAP Business Objects.
- Directory Traversal vulnerability in SAP NetWeaver AS Java Web Container (#2486657): These types of attacks always affect the confidentiality of information, since it allows an attacker to read arbitrary files that shouldn’t be accessed. Its high impact on confidentiality makes its CVSS score the highest of this month. An AS Java Web Container without a proper validation of path information could be impacted due to an attacker reading the content of arbitrary files on the remote server, exposing sensitive data.
CVSS v3 Base Score: 7.7 / 10
Editor Note: This SAP NetWeaver Directory Traversal Vulnerability was added to CISA’s list of Known Exploited Vulnerabilities catalog as CVE-2017-12637. - Cross-Site AJAX Requests vulnerability in SAP BusinessObjects (#2381071): As has happened in the past, this vulnerability is not present in SAP itself but in a third-party Java library that is being used within BusinessObjects. The library has been updated to the fixed version in the latest Service Package. As with any Cross-Site attack, it could lead to client side attacks potentially affecting (with low impact) all confidentiality, availability and integrity of the information.
CVSS v3 Base Score: 7.3 / 10
Summary
It’s been another SAP Notes Day without any critical (Hot News) patch update. Despite it not being a critical month, the high priority notes mentioned above should be treated as soon as possible. Several vulnerability types have been patched this month, including Cross-Site Scripting (XSS are the majority with five notes), Missing Authorization Check, SQL Injection, Code Injection, Denial of Service (DoS), Information Disclosure, Clickjacking, URL Redirection, and Directory Traversal. Almost all bug types are included within this release, despite most of them having a medium priority tag.
Most of the notes (16 of 20) can be automatically installed, which means that it doesn’t require manual steps after note installation. That can help companies make a patch quicker compared to the others. This percentage of automatic notes (80%) is much higher than the previous month, where 57% notes required manual steps for proper protection.
As usual, our researchers who help SAP improve their security are properly acknowledged on the SAP Webpage this month. Onapsis Research Labs is already in the process of updating our product, the Onapsis Security Platform, to incorporate these newly published vulnerabilities. Stay tuned for more information about SAP Security and do not hesitate to reach out to us with if you have further questions about how to protect against the attacks of this month.
