SAP Security Notes August ‘19: SAP JAVA Systems Continuity at Risk From Unauthenticated Attack
Highlights of August’s SAP Security Notes analysis include:
- SAP reacts to vulnerability reported by Onapsis Research Labs—HotNews Note released for fixing Server-Side Request Forgery (SSRF) vulnerability in SAP NetWeaver Application Server Java that can lead to business disruption by shutting down the system
- Highest CVSS rating of the year—Code injection vulnerability in SAP NetWeaver UDDI Server with CVSS score of 9.9 is the most critical of the current year
- This SAP Security Patch Day has the highest number of critical notes in 2019—Three HotNews and two High Priority Notes released, plus one re-released HotNews note
Today, SAP released its monthly patch updates with several critical fixes, including three SAP Security Notes tagged as HotNews (the most critical one in terms of priority). Those notes affect several products, including SAP NetWeaver Application Server for Java, SAP NetWeaver UDDI Server (based on SAP AS JAVA too) and SAP Commerce Cloud (former SAP Hybris Commerce). The last time SAP published three HotNews on the same day was in 2014, so it’s important to pay attention to this month’s release and begin applying the fixes as soon as possible.
These critical bugs include a vulnerability tagged with a CVSS Score of 9.9 and, for the second month in a row, a HotNews reported by the Onapsis Research Labs. There’s also a fourth HotNews, a re-released note published late last month out of schedule. The two fixes affecting SAP Java platforms allow unauthenticated attackers to run remote command executions and potentially disrupt systems operations by shutting it down or collapsing its resources. SAP Java systems usually host web applications that are consumed by users, most probable for regular operations, so a continuity problem can present a severe economic impact in the organization.
Unauthenticated users may convert to SAP Management Console Users
Onapsis researches found and reported a critical vulnerability that was patched today as one of this month’s HotNews. SAP Security Note #2813811, titled “Server-Side Request Forgery (SSRF) in SAP NetWeaver Application Server for Java” has a CVSS of 9.0, since a potential attacker may access the Management Console for SAP Java systems (by stealing user credentials). Unauthenticated users gaining access as administrators of the Management Console could lead to total disruptions of the JAVA Web Portals as well as data access (espionage, leaks) or data modification.
The SAP Management Console provides a way for centralized system management. According to SAP documentation, an administrator (among others) using this tool can:
- Monitor and control (start, stop, or restart) the SAP system and its instances
- Display SAP log and trace files, start profiles, instance parameters, the system environment, SAP environment, Internet Communication Manager (ICM) queue statistics, and more
- Display and control Java processes
Onapsis researchers found this vulnerability in a component of SAP Java systems designed for administrator purposes that may allow an attacker to gain valid credentials for the Management Console (for a background user, not a nominal one). Once done, an attacker may directly connect to it and act as a manager of the system This means that an administrator would be able to execute any task allowed in the Management Console. The worst-case scenarios include remote OS execution on the system and stopping SAP system generation, a denial of service (DoS) Attack.
Even though this vulnerability is critical if successfully exploited, there are a few things that may ensure protection. While installing the patch is always the best option, two other potential protection scenarios (even if the component is vulnerable) include:
- If the system is configured by default, the bug cannot be exploited. That means you should still patch the code, but an attacker won’t be able to exploit it. Unfortunately, the not-default configuration that allows successful exploitation of this attack is recommended as a fix by SAP in several publications, such as SAP Knowledge Base Articles #2577844, #2542492, #2510099, #2506964, #2820566, among others. To check to see if you are not at risk (before applying the patch), you should ensure your “jstartup/service_acl” parameter does not include “sap.com*” (or any mask with ‘*’ that allows this service), as it is by default.
- If you have limited access through HTTP port by setting up ACL files to deny all connections but localhost, you are not at risk. This behaves as a workaround (again, you should still patch the component for the future, but the urgency is not the same). Affected parameters are ‘service/http/acl_file’ and ‘service/https/acl_file’, check SAP Note #1495075 for more data.
A HotNews Month
For the first time this year, SAP has published a Security Note with a CVSS of 9.9. This top scorer, SAP Security Note #2800779, is titled “Remote Code Execution (RCE) in SAP Netweaver UDDI Server (Services Registry)” and warns that attackers can take advantage of a buffer overflow vulnerability to inject code into the working memory. Because of the low complexity of this attack scenario in conjunction with the wide range of possible damages (e.g. information disclosure, data manipulation and destruction) up to the complete control of the product, this Note is considered as the most critical one to be released by SAP in 2019. Fortunately, this vulnerability can easily be fixed by applying the corresponding support packages provided with the note (versions from Netweaver 7.10 to 7.50 are affected and have a patch available).
Code injection is also the subject of the CVSS of 9.0 rated SAP Security Note #2786035, titled “Code injection vulnerabilities in SAP Commerce Cloud”. The described vulnerabilities affect two extensions used with the SAP Commerce Cloud solution. Also, an attacker may be able to take complete control of the application. Please read the ‘Solution’ section of the note carefully as there might be some post-installation steps required after applying the provided patches.
For readers, who might already have missed an update on SAP Security Note #2622660, “Security updates for the browser control Google Chromium,” delivered with SAP Business Client during SAP’s July patch day, SAP has again published the tenth update of this HotNews note on July 23rd. New patches for SAP Business Client have been released that include release 75.0.3770 of the Chromium browser control, fixing 47 security issues in total. In this context, we would like to point out that support for release 6.5 of SAP Business Client has been changed from full to restricted support since the beginning of April 2019. This means that security issues in external components used by SAP Business Client won’t be fixed in release 6.5 anymore if the used version of the external component is out of maintenance (refer to SAP Note #2302074, “Maintenance strategy and deadlines for SAP Business Client / NWBC”, section ‘What does Restricted Support mean for SAP Business Client’ for more data).
Other High Priority Notes in SAP HANA and Kernel
SAP has also released two High Priority Security Notes today. This is the first time in 2019 that there are six critical fixes (summing up High Priority and HotNews notes).
SAP Security Note related to SAP HANA database: The first High Priority vulnerability, fixed in Note #2798243 rated with a CVSS of 7.5, allows an attacker to send malformed connection requests to the SAP HANA instance which crashes the related index server. This leads to the typical symptoms of a DoS attack: long response times, service interruptions and low availability of services, all leading to a poor user experience.
SAP Security Note related to SAP Kernel: SAP Security Note #2798743 with a CVSS of 7.2 (CVE-2019-0349) fixes a Missing Authorization vulnerability in an SAP kernel package and thus preventing attackers from unauthorized information disclosure and data manipulation.
Summary & Conclusions
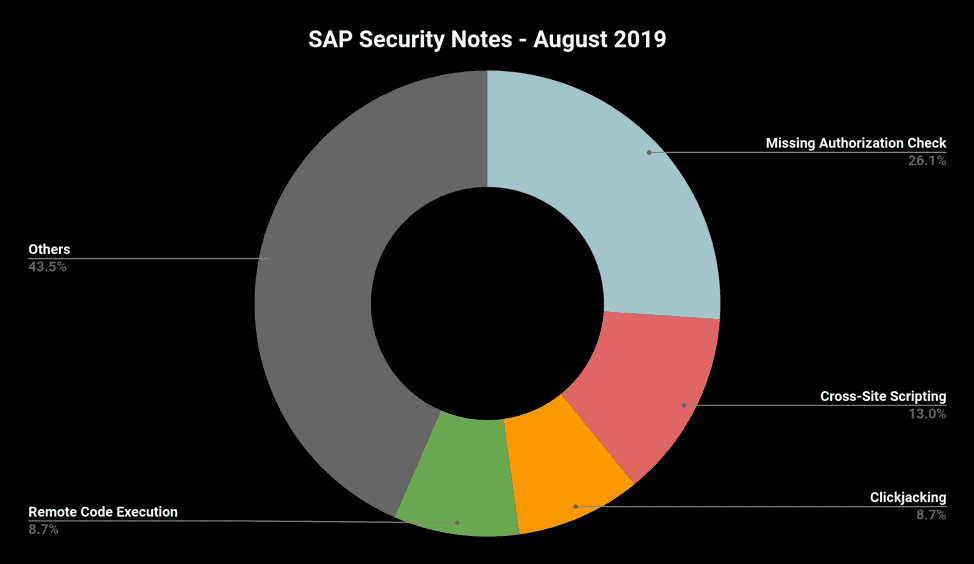
A total of 23 SAP Security Notes were released during August’s Patch Day. The chart below summarizes the types of vulnerabilities, which include: Remote Code Execution, Missing Authorization Check, Cross-Site Scripting and Clickjacking.
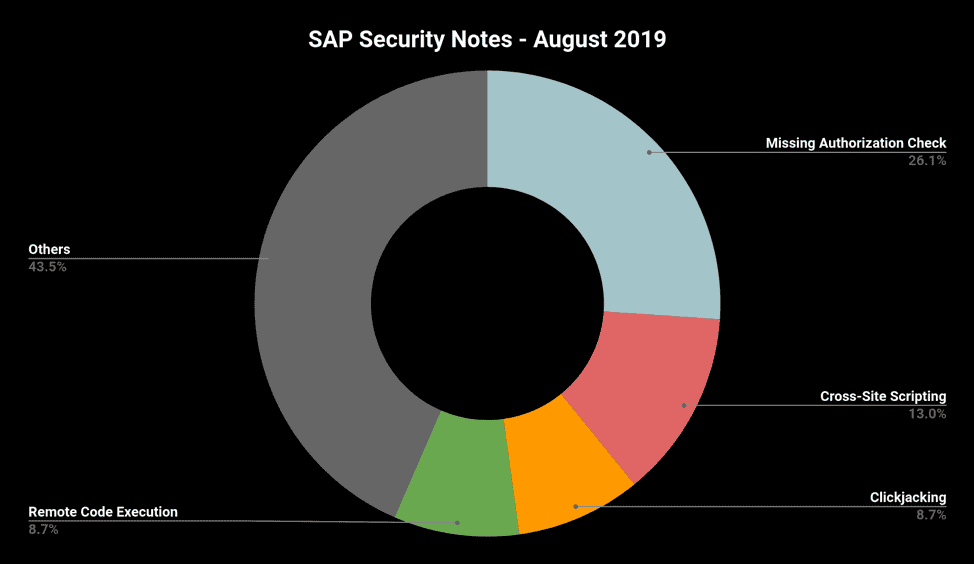
Considering the number of four HotNews and two High Priority Security Notes and taking into account the wide range of attack vectors exploitable in various SAP platforms, the August Patch Day demonstrates impressively the importance of keeping your systems up to date. Fortunately, running a vulnerability and compliance check with the Missing Notes Module in the Onapsis Platform will give you a clear picture of the relevant notes that are currently missing in your SAP landscape.
Our lead Security Researcher, Nahuel Sanchez, was credited by SAP in its acknowledgement webpage for our collaboration this month. The Research Labs is already working to update the Onapsis Platform to incorporate these newly published vulnerabilities into the product so that our customers can check missing notes during their security assessments.
For more information about the latest SAP security issues and to stay in tune with our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
