Protecting Oracle E-Business Suite: Hashed Passwords

Last week, we begin a blogpost series with the objective of reviewing Oracle E-Business Suite Security. The first publication detailed how to activate the Server Security Feature, and in today’s post we will focus on password hashing. We will analyze the different types of hashing and how it is implemented in Oracle E-Business Suite.
Hashing 101
The hash is the result of an algorithm applied to certain text, images or files. It is a fixed result that is also called digest. Hash algorithms have different usages such as authentication or integrity file checks, among others. This blogpost analysis will be based on hash functions used for authentication purposes.
There are some properties which identify hash algorithms:
- With the same input, the hash result should be always the same.
- The input length could be a variable, but the output length will always be the same (whenever you use the same hash algorithm).
- With the minimum change in the input, the hash result should change more than 50% to be considered a good algorithm.
One problem with hash algorithms however, is that when there are two different objects, the result is the same. This scenario is called ‘collision,’ and hash algorithms that have proven collisions tend to be deprecated over time.
Some hash algorithm examples are MD5, SHA1, SHA256, SHA-384, SHA-512, and others. Let’s see some examples.
The password “SYSADMIN” could be stored using SHA-1 and the output will be:
“80e93403887682e0b01ec1ac5c4b9f283a502a94”
Using SHA-256 for the same password “SYSADMIN” the output will be:
“cde01d2db10b2bc2d81a6dc738ccf16f7b99973a57737486903436a685f0e7fa”
Using SHA-512 for the same word “SYSADMIN” the output will be:
“443f1f825d72509132b43e921bc6a45f8b9a56443f02f1904b8bb4c44281848d62e8cccae44b00fdfb348334b52e5c98f593fa2f2a9ed323b1c5b5ccb4011aae”
Note that the digest length is different for each algorithm:
- SHA-1 length is 160 bits
- SHA-256 length is 256 bits
- SHA-368 length is 256 bits
- SHA-512 length is 512 bits
Some implementations combine different hash algorithms, or include a salt to give more security and complexity to the process. The salt is another random data value which is included in the process to mitigate dictionary attacks or rainbow table attacks.
Hashing in Oracle E-Business Suite
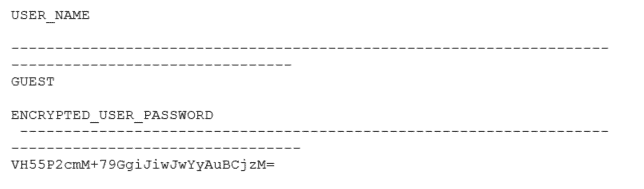
Oracle E-Business Suite uses SHA (Secure Hash Algorithm) combined with the use of the PBKDF2 derivation function to encrypt the passwords in the database. An administrator could check if the encryption is secure or not with the following query to the database: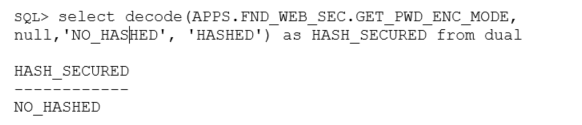
If the result of the query is “NO_HASHED.” This mean that the encryption mode is not considered secure because of the use of SHA-1 to encrypt the password. SHA-1 is no longer considered a secure hashing algorithm due to collisions. For that reason, Oracle has migrated to SHA-2 as default hashing for newer versions. If your system is still using SHA-1, it is strongly recommended to change this setting.
You can also directly query user encrypted passwords. For example, the following query shows GUEST user encrypted password: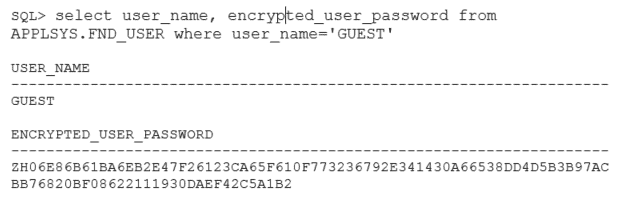
If your system is not using a secure hashing algorithm, you could use AFPASSWD to migrate Oracle E-Business Suite user passwords to a new password hashing scheme. The use of AFPASSWD application changes the password hash stored in the FND_USERS table. The algorithms that are considered secure are the group of SHA-2 algorithms SHA-256, SHA-384, and SHA-512 which are combined with PBKDF2 derivation function.
The options to execute the AFPASSWD are the followings: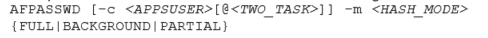
- -c Specify the connection string to use, the Oracle E-Business Suite user, and/or the value of TWO_TASK. This option can be used in combination with others. If it is not specified, default values from the environment will be used.
- -m – Migrates records in the FND_USER table to hash mode using the specified algorithm.
- Specify the hash mode to use. You can specify any of the following advanced hash algorithms:
- SHA-256
- SHA-384
- SHA-512
- Specify the type of advanced hash migration to perform.
- FULL – A full migration migrates all the records in the FND_USER table to the selected hash mode.
- BACKGROUND – A background migration migrates all the records in the FND_USER table to the selected advanced hash mode in the background as a concurrent program named Advanced Hash Migration (AFPASSWD_MIGRATION).
- PARTIAL – A partial migration allows users with an earlier encryption mode to co-exist with users creating new passwords with the selected advanced hash mode. Users on the earlier encryption mode can still log in, but subsequent password changes will switch these users to the selected advanced hash mode.
The following is an example of the execution of AFPASSWD to change the hash algorithm to SHA-512: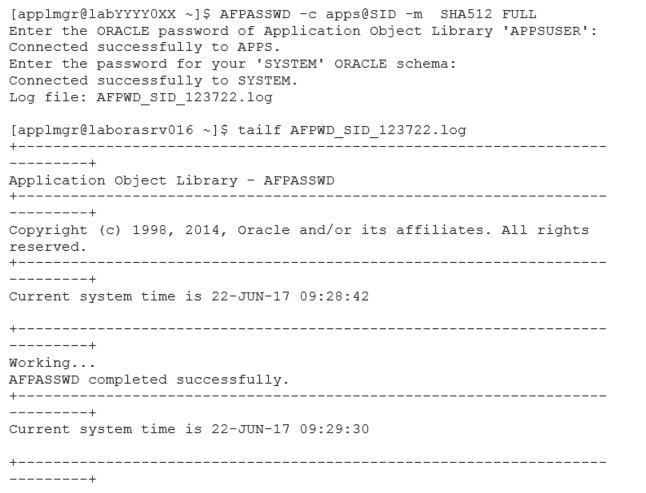
After executing the AFPASSWD application, the password hash will change. For example, this is the output of the same check for GUEST user encrypted password and you can easily check that it changed: