New SAP Exploit Published Online: How to Stay Secure

The Onapsis Research Labs has identified a functional exploit affecting SAP which was published on GitHub, making it publicly available for malicious purposes. This is a fully-functional exploit that abuses CVE-2020-6207 vulnerability, a missing authentication check in EEM Manager, a component of SAP Solution Manager (SolMan). A successful attack exploiting this vulnerability would put an organization’s mission-critical SAP applications, business process and data at risk—impacting cybersecurity and regulatory compliance.
While exploits are released regularly online, this hasn’t been the case for SAP vulnerabilities, for which publicly available exploits have been limited. The release of a public exploit significantly increases the chance of an attack attempt since it also expands potential attackers not only to SAP-experts or professionals, but also to script-kiddies or less-experienced attackers that can now leverage public tools instead of creating their own.
The affected platform, SAP SolMan, is an administrative system used in every SAP environment (similar to Active Directory in Windows). The purpose of SolMan is to centralize the management of all SAP and non-SAP systems that are within an SAP landscape. As an administrative solution, it performs actions such as implementation, support, monitoring and maintenance of all enterprise mission-critical SAP applications, including ERP, CRM, HCM, SCM, BI, financials and others. All systems connected to SolMan are also known as satellite systems. Therefore, due to its nature, it has connections and trust relationships with every SAP system throughout the landscape. If an attacker is able to gain access to SolMan, it could compromise any business system connected to it. Unfortunately, since it doesn’t hold any business information, SAP SolMan is often overlooked in terms of security; in some companies, it does not follow the same patching policy as other systems.
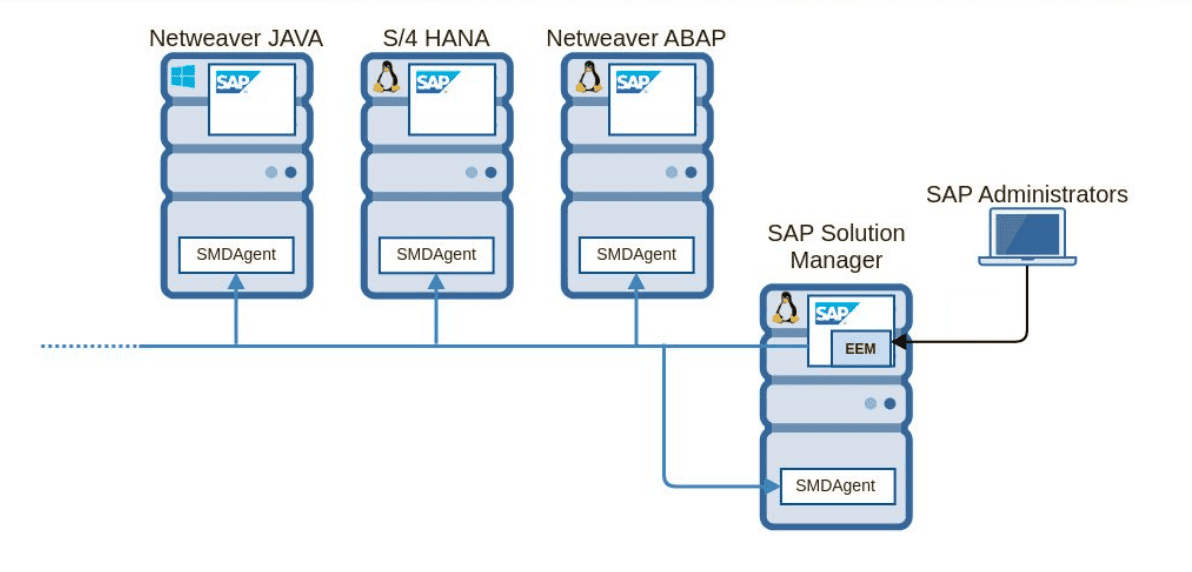
In early 2020, Onapsis Research Labs researchers (Pablo Artuso & Yvan Genuer) identified that in default configurations, unauthenticated remote attackers could be able to execute operating system commands on the satellite systems and achieve full privileges on the associated SAP systems. This vulnerability was properly patched by SAP after Onapsis Report in March 2020 (SAP Security note #2890213), so SAP customers who have proper patching in place shouldn’t be affected by this exploit. It is important to ensure you have properly applied the patch. See further sections to double check whether or not you are protected, how to identify if you have been attacked and more details about how the usage of this exploit against your environment can put critical business processes, data and confidentiality at risk..
It is important to mention that since the release of the exploit, our team has confirmed active scanning activity looking for this specific vulnerability.
What Is the Business Impact?
This vulnerability is rated with a CVSSv3 score of 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), the highest possible score. It affects SAP SolMan and can be exploited by remote unauthenticated attackers having access to the SolMan HTTP(s) port. It would also allow the execution of OS commands in the affected SolMan SMD Agents. This vulnerability was found and reported to SAP by Onapsis Researchers Pablo Artuso and Yvan Genuer, resulting in SAP releasing a HotNews security note/patch.
A successful exploitation could allow a remote unauthenticated attacker to execute highly privileged administrative tasks in the connected SAP SMD Agents (satellite systems connected to SolMan can be affected as well). It is not possible to list everything that can potentially be done in the systems if exploited, since having admin privileged control in the systems or running OS commands basically make it limitless for an attacker. Nevertheless, some (but not limited to) of these malicious tasks can be performed in the previously described exploitation scenarios:
- Shutting down any SAP system in the landscape (not only SAP SolMan)
- Causing IT control deficiencies impacting financial integrity and privacy leading to regulatory compliance violations such as Sarbanes-Oxley (SOX), GDPR and others
- Deleting any data in the SAP systems, including key data that can cause business disruption
- Assigning superuser (e.g. SAP_ALL) privileges to any existing or new user, enabling those users to run business operations that would normally require specific privileges to bypass other Segregation of Duties (SoD) controls
- Reading sensitive data from the database, including employee and customer personal information
Having these vulnerabilities unpatched in the system would disrupt the compliance process, since finance and accounting data can be modified (SOX) or sensitive information can be read from the database (GDPR, HIPAA). Also, some other policies, such as NIST, include control points related to this vulnerability, such as AC-1.70 titled, “Permitted Actions without Identification or Authentication,” which is related to Common Weakness Enumeration CWE-306 titled, “Missing Authentication for Critical Function”.
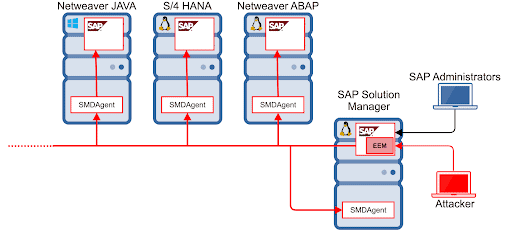
What to Do if Our Organization Is Vulnerable?
If you properly applied the patch (SAP Security Note #2890213, including an available workaround), you are not vulnerable to this exploit. On the other hand if you have not yet applied the patch, an attacker will need network visibility to SolMan as this system is not frequently exposed to the Internet. So for most companies, risk of this exploit should be mostly limited to internal attacks (unless external attackers have already compromised another system and are inside the network. Keep in mind recent national news related to cyberattacks).
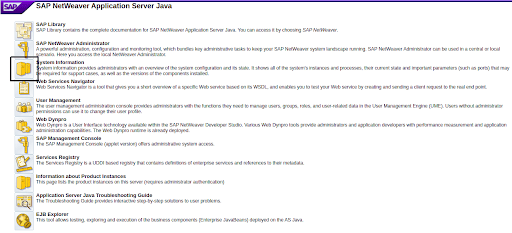
To check if your systems are vulnerable (and you are not an Onapsis Platform customer), checking the component version is the best way to confirm if the patch was applied or not. To check the component version required to be secure in SolMan, you can follow the next steps:
- Go to the main page of your Solution Manager JAVA Stack and select “System Information“
- In the System Information window, select the “Components info” tab and filter by LM-SERVICE
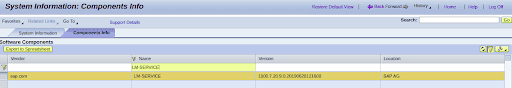
- The ‘Version’ value represents the LM-SERVICE version (1000.7.20.9.0.xxxxxxxxxxx) being
Value 7.20’ represents the component version (being 7.2)
‘9’ represents the Support Package (SP)
‘0’ represents the Patch Level (PL) respectively
So, in this example, the LM-SERVICE version is 720 SP09 with PL00. If you are in any of the following Patch Levels (or above), you are not at risk:
- SOLMANDIAG 720 SP 004 PL 000012
- SOLMANDIAG 720 SP 005 PL 000013
- SOLMANDIAG 720 SP 006 PL 000014
- SOLMANDIAG 720 SP 007 PL 000020
- SOLMANDIAG 720 SP 008 PL 000016
- SOLMANDIAG 720 SP 009 PL 000008
- SOLMANDIAG 720 SP 0010 PL 000002
- SOLMANDIAG 720 SP 0011 PL 000004
Only SAP Solution Manager 7.2 is vulnerable, so older versions are not affected.
For Onapsis Customers
The Onapsis Platform enables customers to easily check if their SolMan systems are vulnerable, by running an assessment on their SolMan assets or by directly checking the output of recent scans. If any of the following issues have been reported, you should apply the patch as soon as possible:
- Missing Authentication Check in SolMan EemAdmin service (OKBID: SAP_76080)
- Missing Authentication Check in SolMan EemAdmin service is fixed, but still vulnerable to unauthorized usage (OKBID: SAP_76081)
- Missing Authentication Check in SolMan EemAdmin service partially fixed and still vulnerable to Remote Code Execution (OKBID: SAP_76082)
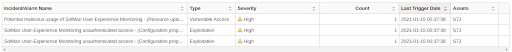
Onapsis customers who have The Onapsis Platform DEFEND capabilities can also check for alerts to see if the exploit was successfully run against their systems, through a set of rules that have been in the product since April 2020 (if you see “SolMan User-Experience Monitoring unauthenticated access” in your Incidents and Alarms reports, contact Onapsis representative for further guidelines.
More Information
- Get a Risk Assessment: Onapsis offers a complimentary Cyber Risk Assessment to identify if you have this specific vulnerability or other critical SAP vulnerabilities including RECON or 10KBLAZE. Request Your Cyber Risk Assessment Now.
- Business Impact: The implications of an attack exploiting this vulnerability is also explained in the Onapsis report: SAP® Security In-depth: Preventing Cyberattacks Against SAP Solution Manager.
- Technical details: Last year, the Onapsis Research team presented at the BlackHat conference about the danger of this specific SAP vulnerability. Read Our White Paper Here.