GRC Tuesdays: Security and IT Risk Mitigation With Pre-Configured Automated Controls

This blog was written by Thomas Frénéhard, Vice-President, Go-To-Market for Finance & Risk Solutions at SAP and was originally published on SAP Community.
A few months ago, I released a blog titled GRC Tuesdays: Integrating Cybersecurity and Enterprise Risk Management to introduce the National Institute of Standards and Technology (NIST) Integrating Cybersecurity and Enterprise Risk Management (ERM) positioning paper. In this publication, NIST explains how cybersecurity risks can be rolled-up to the wider Enterprise Risk Management program and, as such, be included in the overall decision-making process.
Security Controls as a Risk Response Strategy
I was then reminded by readers that I hadn’t provided much guidance on how to keep these cybersecurity risks in check with appropriate responses. Which, admittedly, is still one of risk management’s main objectives. Interestingly, NIST also suggests response strategy types: Accept, Transfer, Mitigate and Avoid.
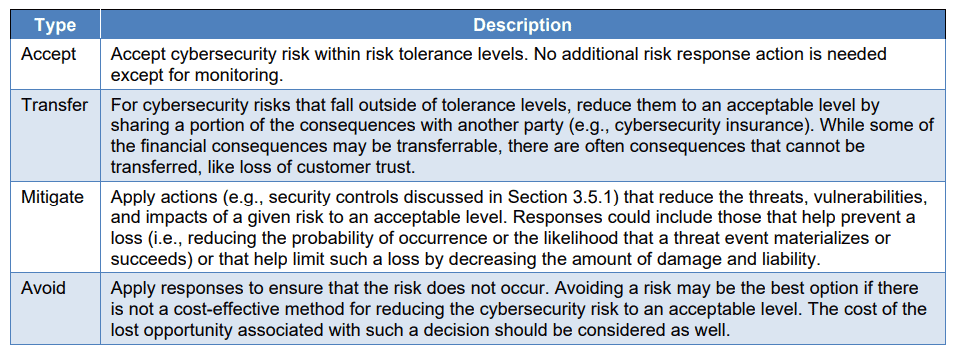
In this blog, I wanted to focus on the “Mitigate” option with a particular focus on the security controls defined by NIST as “safeguards or countermeasures prescribed for an information system or an organization to protect the confidentiality, integrity, and availability of the system and its information”. Of course, NIST is not the only framework that incorporates security and IT control requirements. Think of the Sarbanes-Oxley Act for instance: to help companies manage the IT General Controls, ISACA released its COBIT framework and the IIA its GAIT for Business and IT Risk methodology.
And then there’s Data Privacy and Protection of course with the General Data Protection Regulation (GDPR) in the European Union, California Consumer Privacy Act (CCPA) in the USA, or the Australian Privacy Principle just to name a few or the Payment Card Industry Data Security Standard (PCI DSS) that sets the information security standard for companies managing credit cards for instance. And we all know that it doesn’t stop there. Regulatory superinflations is definitely a sustained trend and so are IT security requirements!
Integration between SAP Process Control and Onapsis Comply: The Winning Combination
If you read this blog, then there’s a chance you will already be aware of SAP Process Control. This is SAP’s end-to-end internal control and cross-regulatory compliance solution.
Recently, in addition to control automation, organizations are also looking for best practice pre-configured content to be embedded directly in this type of solution – especially when it comes to security and IT controls which is increasing in importance within regulations across industries and geographies. To be able to answer this requirement, SAP decided to partner with Onapsis.
Onapsis, a long-term SAP partner that recently joined the exclusive SAP Endorsed Apps program, is a specialized and recognized firm in Cybersecurity. By integrating SAP Process Control and Onapsis, we are able to provide automated out of the box checks/rules that cover a wide range of security and IT General Controls related to different regulations and standards such as SOX, PCI DSS, GDPR, ISO 27001, NIST, NERC and more!
With this integration, the results from the Comply product of the Onapsis Platform are automatically consolidated within the wider internal control framework in SAP Process Control. Hence, providing organizations with a one view of their compliance status.
To discuss in some more details this joint approach, I have invited a guest author today, Brian Tremblay, for a Q&A session.
Brian leads the Compliance Practice at Onapsis where he is responsible for helping customers understand and navigate the challenges and opportunities created by the increasing overlap of compliance, cybersecurity and business continuity related to IT General Controls and regulatory & compliance matters. Prior to his role at Onapsis, Brian has held various audit roles, including Chief Audit Executive. Needless to say, he’s more than an expert in this area and a thought leader!
Thomas (SAP): First, Brian can you tell me a bit about Onapsis and how you create this best in class content?
Brian (Onapsis): Onapsis protects the mission-critical applications that run the global economy, from the core to the cloud. The Onapsis Platform uniquely delivers actionable insight, secure change, automated governance and continuous monitoring for critical systems — Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), Product Lifecycle Management (PLM), Human Capital Management (HCM), Supply Chain Management (SCM) and Business Intelligence (BI) applications — from leading vendors such as SAP, Oracle, Salesforce and others.
Onapsis is headquartered in Boston, MA, with offices in Heidelberg, Germany and Buenos Aires, Argentina. We proudly serve more than 300 of the world’s leading brands, including 20% of the Fortune 100, 6 of the top 10 automotive companies, 5 of the top 10 chemical companies, 4 of the top 10 technology companies and 3 of the top 10 oil and gas companies.
The Onapsis Platform is powered by the Onapsis Research Labs, the team responsible for the discovery and mitigation of more than 800 zero-day vulnerabilities in mission-critical applications. The reach of our threat research and platform is broadened through leading consulting and audit firms such as Accenture, Deloitte, IBM and PwC — making Onapsis solutions the standard in helping organizations protect their cloud, hybrid and on-premises mission-critical information and processes.
Thomas (SAP): What type of content is available with Onapsis Comply and how can this help Compliance and Audit teams?
Brian (Onapsis):
- Out of the box Compliance Frameworks: SOX, GDPR, NIST, PCI DSS, ISACA, ISO 27001, NERC CIP, SAP Security Baselines, and more!
- Fast track IT security compliance programs: Each Compliance Framework is a deep mapping between application-specific checks and the different risks and controls objectives defined by different compliance regulations or standards. Customers main benefit is to gain immediate value thanks to this out of the box content, they can quickly start running a compliance program without the need of further customization or consulting fees. On top of that, our renewed UI makes user experience smooth for customers to easily extend or change the out of the box content in case customers have their own specific requirements.
- Ensure full coverage of security risks via curated content from best in class research lab: The Onapsis Research Labs constantly updates Compliance Frameworks and generates new ones based on changes on regulations, new regulations, or requests from customers. They also maintain and create new checks across multiple applications, keeping up to date with new risks and new controls from internal research projects (e.g.: the 800+ vulnerabilities identified) and the market as well (e.g.: request from a given customer to cover a specific risk that affects most customers).
All these updates are automatically shipped into Onapsis Comply every two weeks.
Thomas (SAP): Why do you think this is a good combination for organizations looking at managing their cyber risks?
Brian (Onapsis):
- Cyber risks don’t occur in silo
- There’s a gigantic perception that Cyber risks are the responsibility of someone like the CISO. While I would certainly advise that there is a sole owner of Cybersecurity risk as multiple owners leads to its own headaches, it is ultimately the responsibility of any senior leader to understand and influence this program based on their unique needs. For example, the Head of Supply Chain needs to clearly understand and articulate their most critical processes and outcomes, so that they can collaborate with the CISO (for example) on prioritization and mitigation of risk. Same thing for the CFO. If protecting the integrity of the Vendor Master File (or any master data in scope for compliance) is a key objective, understanding how Cyber risks can result in modification of the Vendor Master File and bypass role based access control is critical, and unlikely to be fully understood by the CFO. All this said, there is an imperative that all senior leaders and their teams get together to go through the exercise of prioritization of business critical operations and transactions, risk assessment against those (including understanding Cyber Risks) and then what controls are, or likely need to be, in place to mitigate them.
- Strong impact of security risks on compliance programs
- I’ll admit that overall I feel like GRC professionals are a step behind where they need to be on this topic. And I will double click on the Vendor Master Example, and talk a bit about Data Privacy as well. We focus on approaches like role based access control (RBAC) to manage the appropriate level of access to the vendor master file. We extensively look at who can access it and what they can do within it, and sprinkle in separation of duties as well. What we don’t evaluate, at all, is the security risks that can lead to the same undesirable outcomes we are trying to prevent with RBAC. Who can access and change the vendor master file through a misconfiguration, or software vulnerability? Who can write a line of code that bypasses the authorization checks in place? GRC professionals aren’t asking these questions, and this has a significant trickle down effect. If we don’t know the risk, we can’t assess the risk, and as a result we can’t design and implement the appropriate controls. With Data Privacy, where regulations like GDPR prohibit even viewing covered data, the same thought process applies. RBAC may help with ensuring that your ERP or HRM enforces the right controls, but what if that access was viewed, or worse extracted/modified through those same misconfigurations and vulnerabilities?
- Embed security risks within overall internal control program
- So what do you do? You employ state of the art technologies that can be used together to facilitate identification and mitigation of these risks. No single technology can do that, but when you add Comply from Onapsis to Process Control from SAP, you get better visibility into these risks, not only from a security perspective, but also with respect to how they can affect compliance requirements. You get it fast, right out of the gate with preconfigured assessments, that cut across a lot of different regulations, and it is easily customizable for your own needs. In a nutshell, you get better visibility into potential risks and capabilities to determine what risks actually exist right out of the box.
That’s it for this short blog, and I’d like to thank Brian for agreeing to co-author this with me. Due to the scope and nature of this topic, I do believe that we’ll have more blogs coming up so keep an eye open on the GRC Tuesdays.
What about you, how does your organization manage its security and IT controls? Should you be interested in learning more, please feel free to get in touch with either Brian or myself.



